Cisco CCNP TSHOOT Choosing Maintenance and Troubleshooting Applications and Tools

Cisco CCNP TSHOOT Troubleshooting Processes

Define the problem: Utilize an SNMP network monitoring tool. There are numerous products available from various vendors.
Gather Information: There are several things that can be utilize here. Some are simple CLI “show” and “debug” commands.
Analyze: You should have a baseline for your network to compare traffic when a problem surfaces with your baseline. This could assist with determining the problem. One method of baselining your network is by using Cisco Netflow Accounting.
Test the hypothesis: Here you should have very good Configuration Management (CM) which would allow ou to easily test changes and rollback to the previous configuration of the changes do not work.
Cisco CCNP TSHOOT Troubleshooting Processes
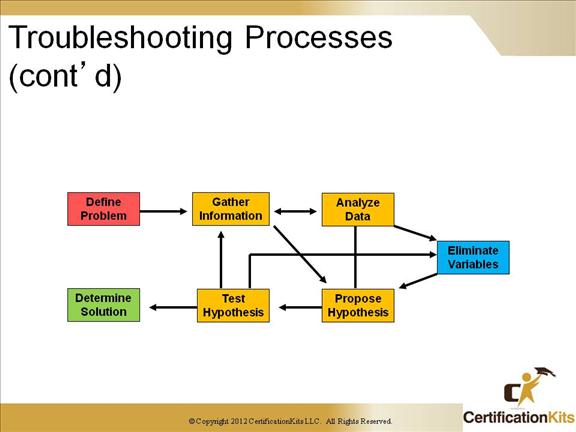
All troubleshooting processes include steps to gather and analyze information, eliminate possible causes, and formulate and testing hypotheses. The time spent on each phase will vary from person to person and is a key differentiator between effective and less-effective troubleshooters.
In a typical troubleshooting process for a complex problem, you would continually cycle between gathering information, analyzing data, eliminate variables then testing and performing the same thing over and over again, each time honing in closer on a possible solution.
Using a structured approach to the troubleshooting process is typically much more efficient then a more or less random way. Also, if your approach has no structure, it is almost impossible to hand over a problem to someone else to troubleshoot without losing nearly all the progress that was made up to that point.
Cisco CCNP TSHOOT Packet Capture and Analysis
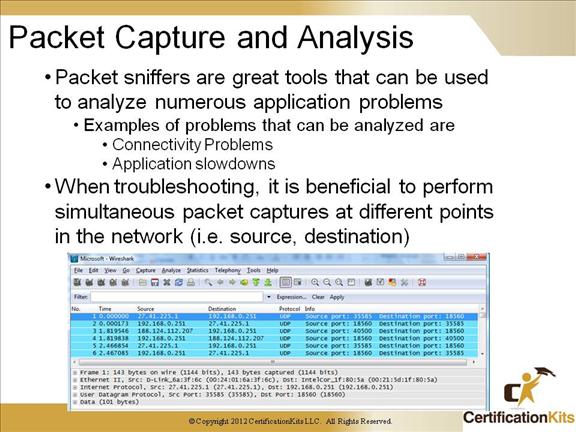
Packet analyzers are essential in troubleshooting application slowdowns as well as connectivity problems with certain applications. Lets take a look at a problem where a user is having problems SSHing to a host. If you are able to ping the remote system it verifies that you have network connectivity. YI the ping succeeds, you can verify if the TCP three way handshake is completing by performing a packet capture by spanning the port connected to the remote host having the same packets sent to a packet analyzer. A commonly used packet analyzer is WireShark. Common problems with not being able to SSH to a remote host are: 1. The SSH service is not running on the server, 2. There is a firewall in the path denying the traffic.
It is beneficial to perform simultaneous packet captures at different points in the network which will provide greater visibility into what the problem may be.
Cisco CCNP TSHOOT SPAN and RSPAN Feature
A SPAN session is an association of a destination port with a set of source ports, configured with parameters that specify the monitored network traffic. You can configure multiple SPAN sessions in a switched network. SPAN sessions do not interfere with the normal operation of the switches. You can enable or disable SPAN sessions with command-line interface (CLI) or SNMP commands. When enabled, a SPAN session might become active or inactive based on various events or actions, and this would be indicated by a SYSLOG message. The “Status” field in the show span and show rspan commands displays the operational status of a SPAN or RSPAN session.
A SPAN or RSPAN destination session remains inactive after system power-up until the destination port is operational. An RSPAN source session remains inactive until any of the source ports are operational or the RSPAN VLAN becomes active.
Cisco CCNP TSHOOT Configuring SPAN
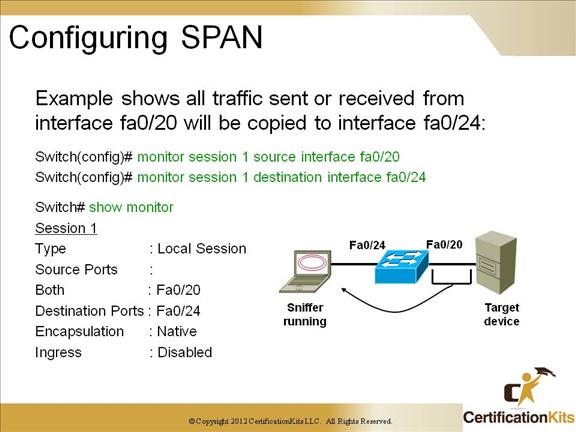
The monitor session command is used to define source and destination interfaces when configuring SPAN.
You can verify your SPAN configuration with the show monitor command.
Cisco CCNP TSHOOT Configuring RSPAN
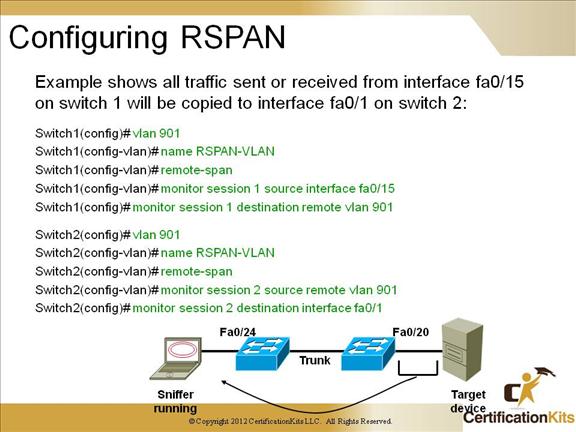
When configuring an RSPAN session, you must first create a VLAN and configure that VLAN as an RSPAN VLAN using the remote-span command within VLAN configuration mode. As with normal SPAN, the monitor session command is used to define source and destination VLANs or interfaces when configuring RSPAN.
You can verify your SPAN configuration with the show monitor command.
Cisco CCNP TSHOOT Using SNMP to Baseline Network Performance and Usage
Simple Network Management Protocol (SNMP) is an Internet-standard protocol for managing devices on IP networks. Devices that typically support SNMP include routers, switches, servers, workstations and more. It is used mostly in network management systems to monitor network-attached devices for conditions that warrant administrative attention. SNMP is a component of the Internet Protocol Suite as defined by the Internet Engineering Task Force (IETF). It consists of a set of standards for network management. Devices contain SNMP Management Information Base (MIB). MIBs describe the structure of the management data of a device subsystem; they use a hierarchical namespace containing object identifiers (OID). Each OID identifies a variable that can be read or set via SNMP.
Cisco CCNP TSHOOT Configuring a Device for SNMP and SNMP Traps
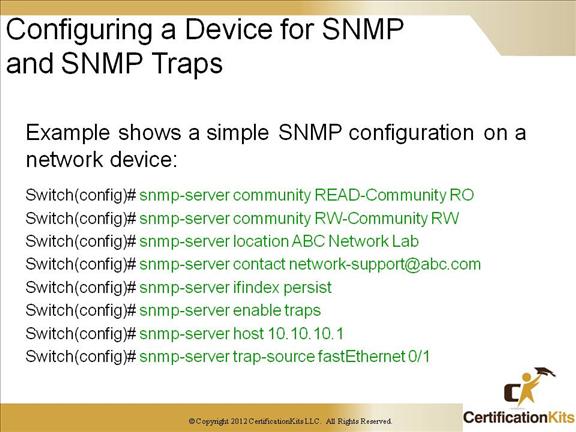
There are multiple versions of SNMP. Namely, version 1, 2, 2c and 3. Both versions 1 and 2 have a number of features in common, but SNMPv2 offers enhancements, such as additional protocol operations. SNMP version 3 (SNMPv3) adds security and remote configuration capabilities to the previous versions.
The configuraton on the slide shows an example of configuring a switch for SNMP version 1.
Cisco CCNP TSHOOT Using NetFlow to Baseline Network Performance and Usage
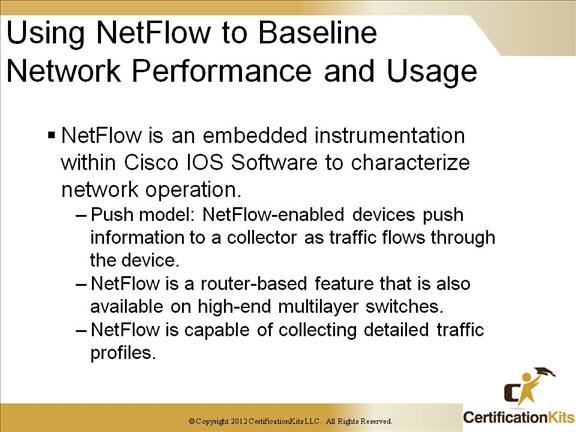
Cisco IOS NetFlow efficiently provides a key set of services for IP applications, including network traffic accounting, usage-based network billing, network planning, security, Denial of Service monitoring capabilities, and network monitoring. NetFlow provides valuable information about network users and applications, peak usage times, and traffic routing. Cisco invented NetFlow and is the leader in IP traffic flow technology.
The basic output of NetFlow is a flow record. Several different formats for flow records have evolved as NetFlow has matured.
Cisco CCNP TSHOOT Configuring a Device for NetFlow Export
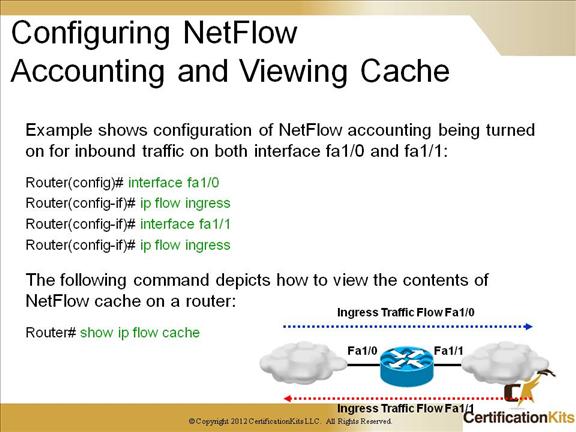
The example on the slide shows collection of Netflow information for interfaces fa1/0 and fa1/1 and viewing the netflow information stored locally on the router.
Cisco CCNP TSHOOT Configuring a Device for NetFlow Export
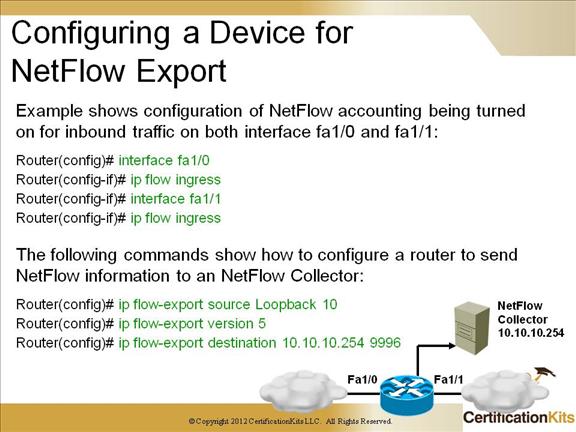
The example on the slide shows collection of Netflow information for interfaces fa1/0 and fa1/1 and sending the Netflow information collected to a Netflow collector residing at IP address 10.10.10.254.
Cisco CCNP TSHOOT Syslog and SNMP Notifications
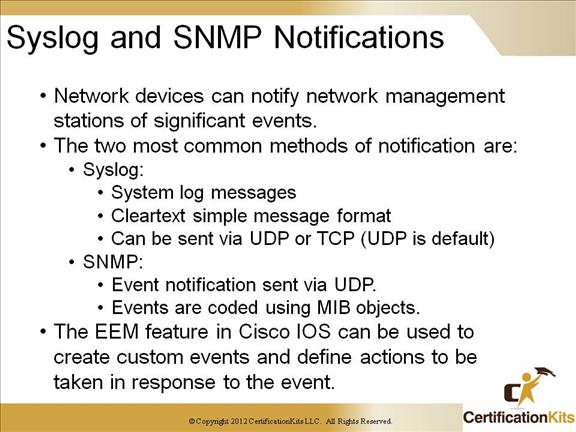
Syslog is a standard for logging program messages. It sends information to a Syslog server via either UDP or TCP port 514 (UDP is the default). It allows separation of the software that generates messages from the system that stores them and the software that reports and analyzes them. It also provides devices which would otherwise be unable to communicate a means to notify administrators of problems or performance.
SNMP is a set of protocols for managing complex networks. It utilizes UDP is a transport means. SNMP capable devices store information about themselves in Management Information Bases (MIBs) and return the data stored to the SNMP requestors.
Cisco CCNP TSHOOT Enabling Syslog
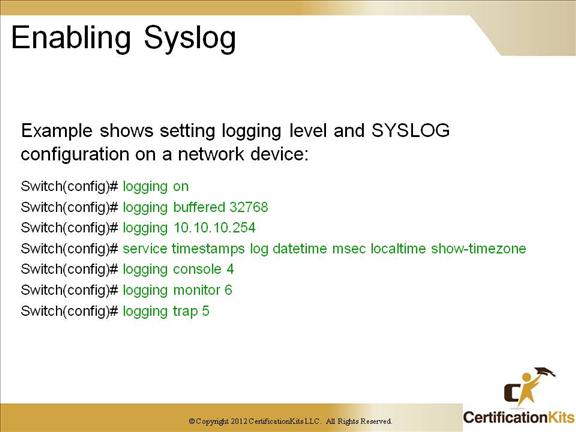
In the example on the slide, the buffered logging is set to a size of 32768. The SYSLOG server is at IP address 10.10.10.254. The logging is set to include a timestamp in the form of date / time to he millisecond displaying the local time with timezone. There are eight different logging levels as follows:
Level Keyword Level Description Syslog Definition
emergencies 0 System unusable LOG_EMERG
alerts 1 Immediate action needed LOG_ALERT
critical 2 Critical conditions LOG_CRIT
errors 3 Error conditions LOG_ERR
warnings 4 Warning conditions LOG_WARNING
notifications 5 Normal but significant condition LOG_NOTICE
informational 6 Informational messages only LOG_INFO
debugging 7 Debugging messages LOG_DEBUG
Console logging is set for warnings, monitor is set for informational and trap is set for notifications. When a logging level is set, messages are sent for that level and lower.
Cisco CCNP TSHOOT Chapter 2 Summary