|
|
| Access Lists and Their Application |
During our CCNA certification studies, we need to understand exactly why we would use an access list to restrict traffic. There is a whole chapter in most CCNA study guides on this topic. So we are going to summarize the concepts Cisco wants you to focus on for the certification exam.
| |
| As a network grows, it becomes more important to manage the increased traffic going across the network. Access lists help limit traffic by filtering traffic based on packet characteristics. Access lists define a set of rules used by routers to identify particular types of traffic. Access lists can be used to filter both incoming and outgoing traffic on a router’s interface. An access list applied to a router specifies rules for only traffic going through the router. Traffic originating from a router is not affected by that router’s access lists. (It is subject to access lists within other routers as it passes through them.) |
| |
| Packet Filtering |
| |
| Access lists can be configured to permit or deny incoming and outgoing packets on an interface. By following a set of conventions, the network administrator can exercise greater control over network traffic by restricting network use by certain users or devices. |
| |
| Application of an IP Access List |
| |
| To establish an access list, you must define a sequential list of permit and deny conditions that apply IP addresses or IP protocols. Access lists filter only traffic going through the router; they do not filter traffic originated from the router. Access lists can also filter Telnet traffic in to or out of the router’s vty ports. |
| |
 |
| |
| Other Access List Uses |
| Access lists allow finer granularity of control when you’re defining priority and custom queues. |
| Access lists can be used to identify “interesting traffic,” which triggers dialing in dial-on-demand routing (DDR). |
| Access lists filter and in some cases alter the attributes within a routing protocol update (route maps). |
|
| |
| Types of Access Lists |
| |
| There are two general types of access lists: |
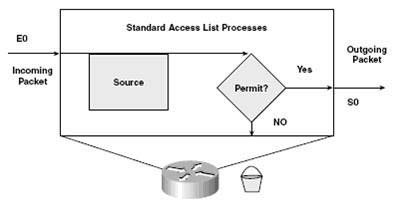
| Standard access lists check the source address of packets. Standard access lists permit or deny output for an entire protocol suite based on the source network/subnet/host IP address. |
|
| |
 |
| |
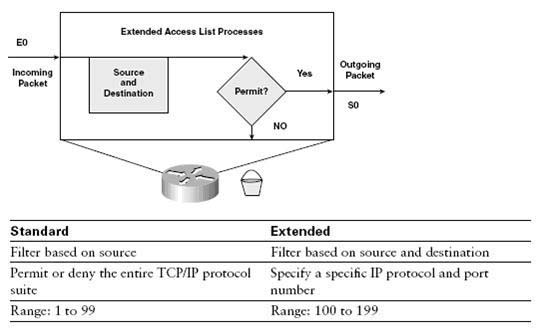
| Extended IP access lists check both source and destination packet addresses. Extended lists specify protocols, port numbers, and other parameters, giving administrators more flexibility and control. |
|
| |
 |
| |
| Access List Process Options |
| Inbound access lists—Incoming packets are processed prior to being sent to the outbound interface. If the packet is to be discarded, this method reduces overhead (no routing table lookups). If the packet is permitted, it’s processed in the normal way. |
| Outbound access lists—Outgoing packets are processed by the router first and then are tested against the access list criteria. |
|
| |
| Permit or Deny Process |
| |
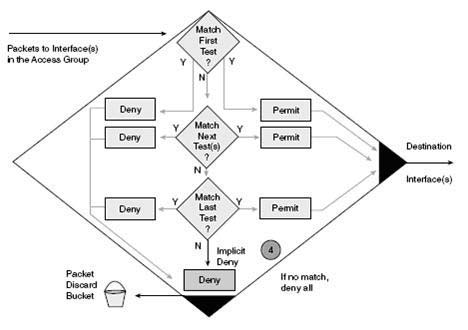
| Access list statements are operated on one at a time from top to bottom. After a packet header match is found, the packet is operated on (permitted or denied), and the rest of the statements are skipped. If no match is found, the packet is tested against the next statement until a match is found or the end of the list is reached. An implicit deny statement is present at the end of the list. (All remaining packets are dropped.) Unless there is at least one permit statement in an access list, all traffic is blocked. |
| |
 |
| |
| Guidelines for Implementing Access Lists |
| Be sure to use the correct numbers for the type of list and protocols you want to filter. |
| You can use only one access list per protocol, direction, and interface. A single interface can have one access list per protocol. |
| Put more-specific statements before more-general ones. Frequently occurring conditions should be placed before less-frequent conditions. |
| Additions are always put at the end of the access list. You cannot selectively add or remove statements in the middle of an access list. |
| Without an explicit permit any statement at the end of a list, all packets not matched by other statements are discarded. Every access list should include at least one permit statement. |
| An interface with an empty access list applied to it allows (permits) all traffic. Create your statements before applying the list to an interface. |
| Access lists filter only traffic going through the router. |
|
| |
| Protocol Access List Identifiers |
| |
| The access list number entered by the administrator determines how the router handles the access list. The arguments in the statement follow the number. The types of conditions allowed depend on the type of list (defined by the access list number). Conditions for an access list vary by protocol. You can have several different access lists for any given protocol, but only one protocol is allowed on any access list (one protocol per direction per interface). |
| |
| TCP/IP Packet Tests |
| |
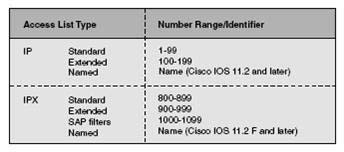
| For TCP/IP packets, access lists check the packet and upper-layer headers for different items (this depends on the type of access list, standard or extended). Standard access lists are assigned a number in the range 1 to 99. Extended access lists use the range 100 to 199. As soon as a packet is checked for a match with the access list statement, it is either permitted to an interface or discarded. |
| |
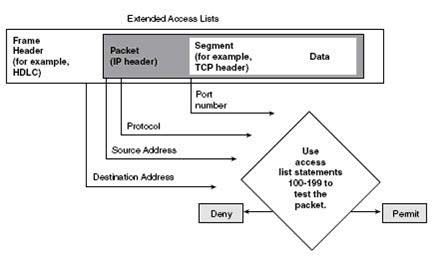 |
| |
| Wildcard Masking |
| |
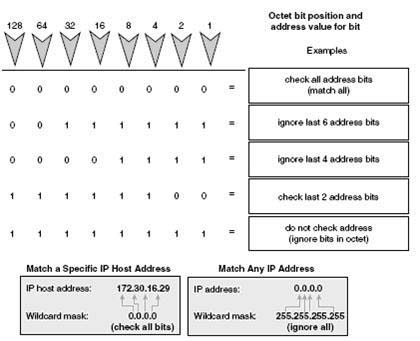
| It is not always necessary to check bytes within an address. Wildcard masking identifies which bits should be checked or ignored. Administrators can use this tool to select one or more IP addresses for filtering. Wildcard masking is exactly opposite of subnet masking. |
| A wildcard mask bit 0 means check the corresponding bit value. |
| A mask bit 1 means do not check(ignore) that corresponding bit value. To specify an IP host address within a permit or deny statement, enter the full address followed by a mask of all 0s (0.0.0.0). To specify that all destination addresses will be permitted in an access list, enter 0.0.0.0 as the address, followed by a mask of all 1s (255.255.255). |
|
| |
 |
| |
| Abbreviated Commands in Wildcard Masking |
| |
| You can use abbreviations rather than typing an entire wildcard mask: |
| Checking all addresses-To match a specific address, use host. For example, 172.30.16.29 0.0.0.0 can be written as host 172.30.16.29. |
| Ignoring all addresses-Use the word any to specify all addresses. For example, 0.0.0.0 255.255.255.255 can be written as any. |
|
| |
| Access Lists and Their Applications Summary |
| Access lists filter packets as they pass through the router. |
| The two general types of access lists are standard and extended. Standard lists filter based on only the source address, and extended lists filter based on source and destination addresses, as well as specific protocols and numbers. |
| Access lists can be set to either inbound or outbound. For inbound access lists, the packets are processed first and then routed to an outbound interface (assuming that the filter passes them). In outbound access lists, the packets are sent to the interface and then routed. |
| If a packet meets a permit statement’s criteria, it is passed to the next statement. If a packet meets a deny statement’s criteria, it is immediately discarded. |
| More-restrictive statements should be at the top of the list. |
| Only one access list per interface, per protocol, per direction is allowed. |
| Every access list should have at least one permit statement. |
| For IP, standard access lists use the number range 1 to 99, and extended access lists use 100 to 199. |
| Wildcard masking is used to filter single IP addresses or blocks of addresses. |
|
| |
| Continue on to the Access List Configuration Article |
| |






