The Internet Protocol Suite is a framework that defines a set of general design guidelines and implementations of specific networking protocols to enable computers to communicate over a network. RFC 1122 describes the Internet Protocol Suite architectural model which commonly is referred to as the TCP/IP Suite Model. To communicate over the Internet, a host must implement the layered set of protocols comprising the Internet protocol suite.
The figure below shows the TCP/IP model that comprises of four layers.
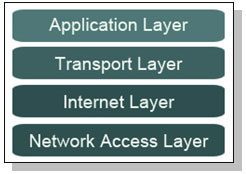
The Network Access Layer also is known as the Link Layer or the Media Access Layer defines protocols and specifications that must be implemented by the host to communicate with its directly connected network. The primary responsibility of this layer is to define how a node connects to the local network. The local network can use technologies such as Ethernet, Token Ring, or Fiber Distributed Data Interface (FDDI) and the node has to follow the rules for sending and receiving the data according to the specific network it is attached to. These technologies are responsible for functions such as physical layer addressing, media access control, layer 2 framing of datagrams received from the Internet layer etc.
For all TCP/IP communications to occur, the nodes attached to the network must have an address that uniquely identifies them on the network. This address is known as the Physical or Hardware Address and is burned in the network interface card (NIC) of the node. For a TCP/IP frame to be delivered it must contain a source address that identifies the node sending the data and a destination address that identifies the node for which data is intended. When a node receives a frame it will examine the header and check the destination address, if the destination address matches the address specified on its network interface card then the frame will be passed up the stack for processing.
The Internet Layer describes a group of methods, protocols, and specifications which are used to transport datagrams (packets) from a host across network boundaries, if necessary, to the destination host specified by a network address (IP address) which is defined for this purpose by the Internet Protocol (IP). Every machine on the Internet whether it is a host machine accessing services or a server providing services needs a unique IP address that identifies that system on the Internet. IP version 4 (IPv4) is the current version of Internet Protocol being used on the Internet. IPv4 defines a 32-bit address which allows the possibility of 4,294,967,296 unique addresses, however, due to the rapid growth of the Internet this space is limited. IP version 6 (IPv6) which is intended to be the successor of IPv4 has a 128-bit address space which vastly larger than IPv4 address space.
All Internet transport protocols use the Internet Protocol (IP) to carry data from source host to the destination host. IP is a connectionless or datagram internetwork service, providing no end-to-end delivery guarantees.
The Internet Protocol is the primary protocol at the Internet layer of the TCP/IP stack. It is responsible for determining the source and destination IP addresses of every packet. The hardware address on the Network Access Layer refers to the physical network card, while the IP address is a logical address that the network administrator assigns to the host. Every host on a TCP/IP network has a unique IP address. A portion of the IP address describes the IP network that the host is on, and the other portion describes the unique host address on that network.
The Internet Protocol determines whether the destination is on the local network or remote network as compared to the source host. The destination is on the local network if it is on the same network, and it is remote if it is on another network. Internet Protocol can make this determination based on the IP address of the destination and the subnet mask of the source host. The subnet mask is a required parameter of every TCP/IP address that is used to separate the network and host portions of that address.
The Internet Protocol also needs to determine how to get a packet to the destination. If the destination is addressed to a host on the local network, it can communicate directly with the destination host. If the host is on a remote network, it needs to send the packet through the default gateway. A default gateway is the address of a host on the network that offers a route off of the network. It is a device connected to the edge of the network and acts as the gateway to other networks.
The Internet Layer contains several protocols as listed below
- Internet Protocol (IP)
- Internet Control Message Protocol (ICMP)
- Internet Group Message Protocol (IGMP)
The Transport Layer also is known as the Host-to-Host layer provides end-to-end communication services for applications. The protocols at the Transport layer deliver data to and receive data from the Transport layer protocols of other hosts. The other host can be on the local network or on a network thousands of miles away There are two primary transport layer protocols
- Transmission Control Protocol (TCP)
- User Datagram Protocol (UDP)
TCP is a reliable connection-oriented transport service that provides end-to-end reliability, resequencing, and flow control. Connection-oriented means that a connection is established as the communication begins. During this connection, certain information is exchanged to set the parameters of the communication. End-to-End reliability means that an acknowledgment will be sent back to the sending host throughout the communication to verify receipt of the packets. As each segment of data is received at the destination, an acknowledgment is sent to the sender within a specified period. If an acknowledgment is not sent within that time, the sender resends the data. If the receiver of the data gets the data in a damaged condition, the damaged packet is simply discarded. The recipient sends no acknowledgment for the damaged packet, and because the sender receives no acknowledgment, the data is re-sent. TCP is a connection-oriented protocol because the connection is set up and used for the entire conversation. As packets are moved between the hosts having the conversation, TCP provides the connection. Each packet has a TCP header that includes sequence numbers, acknowledgment numbers, addresses, and other pieces of connection information. TCP is also responsible for dividing the data into smaller packets if the data is too large to fit into a single packet. TCP on the destination host reassembles the packets so that the data is presented to the Application layer all put back together. After a packet is sent, the sending host waits for an acknowledgment before sending more data. This is the feature of TCP that guarantees delivery of packets. If an acknowledgment is not received at the sending host, the sender resends the packet. Every TCP packet that is received by the receiver triggers TCP to send back an acknowledgment packet. If the sending host does not receive the acknowledgment, then something must have gone and TCP on the host simply retransmits the missing packet.
UDP is a connectionless datagram transport service that provides connectionless, unreliable communication. Connectionless means that no connection is established before data transfer begins. The sending host does not send any setup packets to the destination; it just starts sending. Therefore unlike TCP, UDP does not need to set up a connection and does not use acknowledgments. UDP is used by technologies and applications that do not require the complexity of TCP and when they need quick communication where using TCP will be unnecessary. Most Voice over IP protocols and technologies use UDP for transport as using TCP will unnecessary include complexities and slowness.
The Application Layer is the top-most layer, it refers to the higher-level protocols used by applications for network communication such as File Transfer Protocol (FTP), HyperText Transfer Protocol (HTTP) and Simple Mail Transfer Protocol (SMTP). The Application Layer is where the request for data/services are processed. Protocols at this layer are waiting for requests to process, and they are all listening at their respective ports. A port is a number that the application at the Application layer uses as a send-and-receive address. As a packet is moving up through the stack on its way to the Application layer, the Transport layer directs the packet to the appropriate port.
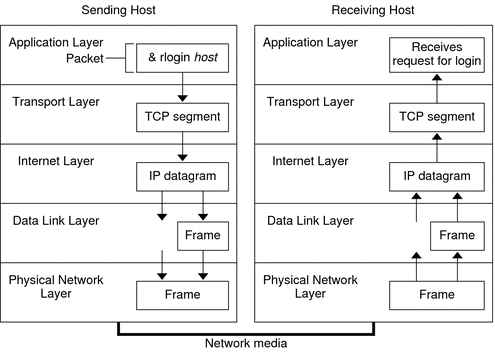
How the TCP/IP Protocols Handle Data Communications
When a user issues a command that uses a TCP/IP application layer protocol, a series of events is initiated. The user’s command or message passes through the TCP/IP protocol stack on the local system. Then, the command or message passes across the network media to the protocols on the remote system. The protocols at each layer on the sending host add information to the original data. Protocols on each layer of the sending host also interact with their peers on the receiving host.
The figure below shows how two hosts communicate using the TCP/IP protocol stack.
Today we covered the Internet Protocol Suite and studied its framework and architecture. In upcoming lessons, we will cover specific protocols and technologies in the Internet Protocol Suite.
