PortFast
If the End user PC connected to an access port of a switch is powered on it will take around 52 seconds (in the default configuration) for the port to be usable as the port transitions STP port states (from blocking to forwarding). During this time, the switch port is totally unusable for data forwarding. Cisco came up with a technique to by-pass the listening and learning state and putting the port directly in the forwarding state. Another characteristic of PortFast is that Topology Change Notification (TCN) BPDU is never sent for port up/down events. The advantage is simplified TCN transmission in a large network when a lot of end-user workstations are coming up or shutting down.
STP is never disabled on switch ports with PortFast enabled. If for any reason BPDU is heard, the port losses the PortFast status.
Warning: Never enable PortFast on ports connecting to other switches or hubs. This could lead to bridging loops and broadcast storms since the switch port never goes through the listening and learning state of STP.
Configuration
The configuration is simple. It can be done either globally or per-interface basis. When enabling globally, portfast is enabled on all non-trunking ports.
Globally:
Step-1: configure terminal
Step-2: spanning-tree portfast default
Step-3: exit
Per-Interface:
Step-1: configure terminal
Step-2: interface
Step-3: spanning-tree portfast
Step-4: end
BPDU Guard
PortFast and BPDU guard are linked together. PortFast allows transition to forwarding state directly, but there are still chances of bridging loops, however, a loop can be detected only in a finite amount of time (the STP states).
PortFast is enabled on ports where loops are never expected because they connect end-users, not switches. But if for any reason (by mistake… off-course), another switch is connected to the PortFast enabled port there is a chance of bridging loop.
But what if you are a service provider and a customer has connected his/her switch to PortFast enabled port? The worst thing is that the customer switch announces a SUPERIOR BDPU and becomes the NEW Root Bridge. The BDPU guard was developed to protect the integrity of STP topology. Figure-1 and Figure-2 illustrates the concept. When BPDU guard is enabled, traffic flows through the SP core.
If a BPDU is ever heard on a PortFast port (superior or not) and BPDU guard is enabled, the port is put in Error Disabled (errdisable) state or Shutdown depending on how BPDU guard is configured.
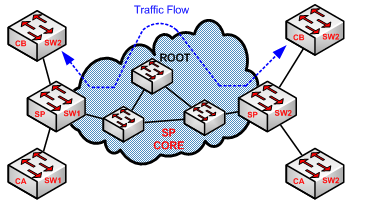
FIGURE-1: BPDU Guard Enabled and Traffic Flow
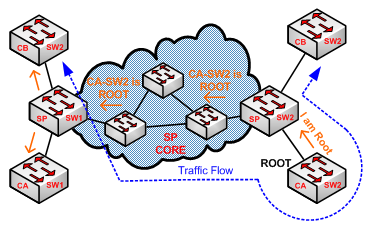
FIGURE-1: BPDU Guard Disabled and Traffic Flow
If enabled globally, the port is put in shutdown state. If enabled per-interface basis, the port is put in errdisable state. In any case, errdisable recovery must be done either manually or through errdisable recovery timeouts.
Warning: BPDU guard should never be implemented on Uplink ports where Root Bridge is located. In the case of multiple uplinks, BPDU guard must be disabled to accept legitimate BPDUs.
Configuration
Globally:
Step-1: configure terminal
Step-2: spanning-tree portfast bpduguard default
Step-3: exit
Per-Interface:
Step-1: configure terminal
Step-2: interface
Step-3: spanning-tree bpdu guard enable
Step-4: end
