In preparation of our CCNA exam, we want to make sure we cover the various concepts that we could see on our Cisco CCNA exam. So to assist you, below we will discuss CCNA Access List Configuration.
|
|
||||||||||||||||||||||||
|
|
||||||||||||||||||||||||
| Access List Configuration | ||||||||||||||||||||||||
| Principles of Configuring Access Lists | ||||||||||||||||||||||||
| Access lists are processed from top to bottom, making statement ordering critical to efficient operation. Always place specific and frequent statements at the beginning of an access list. Named access lists allow the removal of individual statements (but no reordering). To reorder statements, you must remove and re-create the whole list with the proper statement ordering. Use a text editor to create lists. Remember that all access lists end with an implicit deny all statement. | ||||||||||||||||||||||||
| Access List Syntax | ||||||||||||||||||||||||
| The syntax for a standard and extended IP access lists is access-list access-list-number {permit | deny} source [mask]. access-list access-list-number {permit | deny} protocol source source-wildcard [operator port] destination destination-wildcard [operator port] [established] [log] operator port can be less than, greater than, equal to, or not equal to a port number. established (used for inbound TCP only) allows only established connections to pass packets. |
||||||||||||||||||||||||
| log sends a logging message to the console. After the statements are added, they are applied to an access group using the following syntax: ip access-group access-list-number {in | out} Here is the procedure for configuring extended IP access lists: |
||||||||||||||||||||||||
| RouterA>enable RouterA#access-list 101 deny tcp 172.16.4.0 0.0.0.255 72.16.3.0 0.0.0.255 eq 21 RouterA#config term RouterA(config)#interface ethernet 0 RouterA(config-if)#access group 101 in RouterA(config)#exit RouterA#show ip interface |
||||||||||||||||||||||||
| Named Access Lists | ||||||||||||||||||||||||
| Named IP access addresses (Cisco IOS Release 11.2 and later) allow alphanumeric strings as identifiers rather than numbers. Named access lists can be standard or extended. Named IP access lists also allow you to delete individual statements from an access list. You should use named access lists when more than 99 standard or extended access lists are configured on any router. Duplicate names are not allowed on any one router. (You can use the same name on two different routers.) | ||||||||||||||||||||||||
| Guidelines for Placing Access Lists | ||||||||||||||||||||||||
| Extended access lists can block traffic from leaving the source. They should be as close as possible to the source of the traffic to be denied. Standard access lists block traffic at the destination. They should be as close as possible to the destination of the traffic to be denied. | ||||||||||||||||||||||||
| Virtual Terminal Access Lists | ||||||||||||||||||||||||
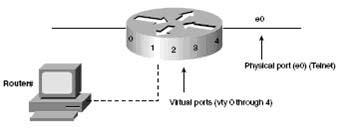
| In addition to physical ports, devices also have virtual ports (called virtual terminal lines). There are five such virtual terminal lines, numbered vty 0 through vty 4. Standard and extended access lists do not prevent router initiated Telnet sessions. Virtual terminal access lists can block vty access to the router or block access to other routers on allowed vty sessions. Restrictions on vty access should include all virtual ports, because users can connect through any vty port. The syntax for a vty access list is line vty {vty# | vty-range}. After you add the vty statements, you assign them to the router with the following command: access-class access-list-number {in | out} Specifying in prevents incoming Telnet connections, and out prevents Telnet connections to other routers from the vty ports. |
||||||||||||||||||||||||
 |
||||||||||||||||||||||||
| Access List Configuration Summary | ||||||||||||||||||||||||
|
||||||||||||||||||||||||
We hope you found this Cisco certification article on access lists helpful. We pride ourselves on not only providing top notch Cisco CCNA exam information, but also providing you with the real world Cisco CCNA skills to advance in your networking career.
We hope you found this Cisco certification article helpful. We pride ourselves on not only providing top notch Cisco CCNA exam information, but also providing you with the real world Cisco CCNA skills to advance in your networking career.
