An Extended ACL is created with the access-list command and then applied to the interface using the access-group command. Standard ACL syntax and description are shown below
|
Ciscoasa(config)# access-list access-list-number {deny | permit} protocol source-address |
|
Syntax Description |
|
|
access-list-number
|
Identifies an access list by number as a standard or extended list. Also allows the creation and separation of multiple access lists.
|
|
deny
|
Denies access if the conditions are matched. |
|
permit
|
Permits access if the conditions are matched. |
|
Protocol
|
Name or Number of an Internet Protocol such IP, TCP, UDP, EIGRP, OSPF etc
|
|
source
|
Specifies the IP address/network to match on the source IP address of the Packet. Use the any keyword as an abbreviation for a source and source-wildcard of 0.0.0.0 255.255.255.255.
|
|
source-wildcard
|
(Optional) Wildcard bits to be applied to the source
|
|
destination
|
Specifies the IP address/network to match on the destination IP address of the Packet. Use the any keyword as an abbreviation for a destination and destination-wildcard of 0.0.0.0 255.255.255.255.
|
|
destination-wildcard
|
(Optional) Wildcard bits to be applied to the destination
|
|
log |
Causes an informational logging message about the packet that matches the entry to be sent to the console.
|
|
Log-input |
(Optional) Includes the input interface and source MAC address or VC in the logging output.
|
In Cisco IOS the Extended ACLs can have numbers in range of 100-199 and 2000-2699. Extended ACLs should be applied close to the source of the packets so that a packet is denied near the source to save router resources and bandwidth rather then it being forwarded close to the destination and eventually being denied. We will use the network depicted in figure below to explain this concept.
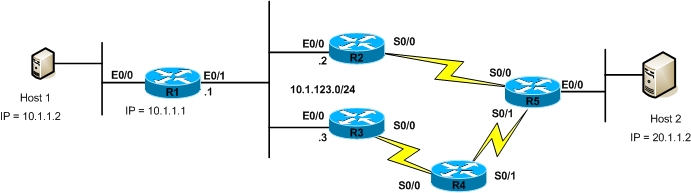
Our task is to configure the network such that host 20.1.1.2 cannot access 10.1.1.2, first we will create an access-list as shown below
Ciscoasa(config)# access-list 101 deny ip host 20.1.1.2 host 10.1.1.2
Ciscoasa(config)# access-list 101 permit ip any any
and then we will apply this access-list to an interface which will process incoming packets and if there is match it will drop the packets. Since Extended ACLs include enough information to properly match the right packet when can place them anywhere in the network, but common sense dictate us to place them close to the source for efficiency, as placing them far from source will unnecessarily consume network resources.
Configuration Examples
This example focuses on applications of Extended ACLs. We will use the network in the figure above to explain various configuration examples of Extended ACLs. First and foremost we will use an Extended ACL to restrict host 1 to access the FTP Server with IP address 20.1.1.10 connected to LAN on R5 E0/0 interface.
R1(config)# access-list 101 deny tcp host 10.1.1.2 host 20.1.1.10 eq FTP
R1(config)# access-list 101 permit ip any any
R1(config)# interface ethernet0/0
R1(config)# access-group 101 in
The configuration shown above configures R1 to restrict FTP packets sourced from host 10.1.1.2 and destined to the FTP Server 20.1.1.10 and allow all other communication.
There also several other examples of Extended ACLs due to their ability to match multiple fields of a packet. For example we can configure an ACL on R1 to completely deny host 10.1.1.2 thereby isolating it from the complete internetwork.
R1(config)# access-list 110 deny ip host 10.1.1.2 any
R1(config)# access-list 110 permit ip any any
R1(config)# interface ethernet0/0
R1(config)# access-group 101 in
The configuration shown above configures R1 to restrict any packets sourced from host 10.1.1.2 and allow all other communications thereby isolating the host from the internetwork.
This brings us to the end of this lesson in which we covered Extended ACLs, it is very important that we both have the theoretical and practical knowledge of Extended ACLs to master the topic.
