- Internet Key Exchange (IKE) is a protocol used to set up a security association (SA). IKE is responsible for securely exchanging encryption keys using Diffie–Hellman key exchange, to authenticate IPSec peers using pre-shared or Public Keys and negotiating IPSec SA. IKE consists of two phases, Phase 1 and Phase 2 described below
- Phase 1: In this phase potential IPSec peers are authenticated and an IKE/ISAKMP SA is established using Diffie–Hellman key exchange. A secure channel is established between potential IPSec peers using encryption, authentication and hash algorithms. The purpose of this phase is to provide a secure channel between peers for secure Phase 2 negotiation
- Phase 2: In this phase the potential IPSec peers will use the secure channel established in Phase 1 to negotiate and establish IPSec SAs using ESP or AH protocols to protect the actual data traffic.
- Diffie-Hellman algorithm was published by Whitfield Diffie and Martin Hellman in 1976. It establishes a shared secret that can be used for secret communications by exchanging data over a public network. We will explain this using an example in which two parties A and B wants to communicate with each other securely. In order to achieve this secure communication, A needs to establish a session key with B, but they have to somehow agree on a shared key over a public medium that is insecure.To make matters worse, an Intruder wishes to monitor this communication. The algorithm has two system parameters, p and g. The parameters are both public and, therefore, may be used by all the users in a system. Parameter p is a large prime number and parameter g (usually called a generator) is an integer less than p, which is capable of generating every element from 1 to p1 when multiplied by itself a certain number of times modulo the prime p.First, A generates the random private value a and B generates the random private value b. Then they derive their public values using parameters p and g and their private values. A’s public value is X=ga mod p and B’s public value is Y=gb mod p. They then exchange their public values. Finally, A computes kab=(gb)a mod p, and B computes kba=(ga)b mod p. Because kab=kba=k, A and B now have a shared secret key k. The protocol depends on the discrete logarithm problem for its security. It assumes that it is computationally infeasible to calculate the shared secret key k=gab mod p given the two public values ga mod p and gb mod p when the prime p is sufficiently large. Although all of this has been accomplished with Intruder monitoring, he cannot determine the value of the shared key
- A security association (SA) is a relationship between two or more entities that describes how the entities will use security services to communicate securely.
- Encapsulating Security Payload (ESP) is used to provide confidentiality, data integrity, authentication and anti-replay services. ESP encrypts (using a variety of encryption algorithms such as DES, 3DES and AES) the original payload and encapsulates the packet between an ESP header and trailer. ESP uses IP Protocol number of 50
- Authentication Header (AH) is used to provide connectionless integrity, data authentication and optional relay protection. Unlike ESP, AH does not provide confidentiality. AH uses IP Protocol number of 51
- Phase 2 Connection Modes: There are two types of modes that AH and ESP can use to transport data between two entities
- Transport Mode: In this mode, AH or ESP header is inserted between the IP header and upper layer protocol header. The IP header is the same as the original header except for the Protocol Field which is either 50 (ESP) or 51 (AH). When using Transport mode the two entities over which the VPN is established must be reachable, the IPSec and IP endpoint are same when using transport mode, and therefore it used to protect host-host communications.
- Tunnel Mode: In this mode, the original IP packet is encapsulated in another IP datagram and the AH or ESP header is inserted between outer and inner headers. Because of this encapsulation IPSec and IP endpoints can be different and a gateway router at each site can provide secure service on behalf of hosts at each site. Site-to-Site VPN uses tunnel mode to secure communications between hosts at different sites.
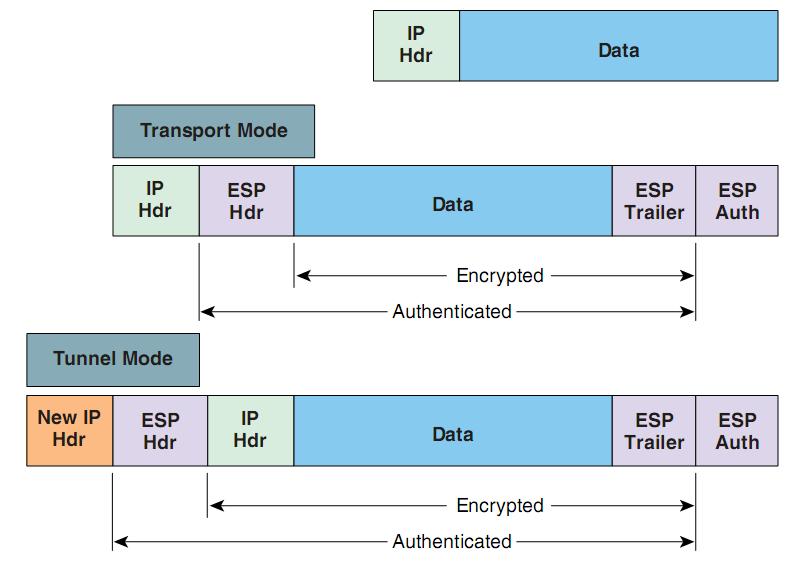
Figure above illustrates how ESP encapsulates an IP Packet in transport and tunnel mode
SSL (Secure Sockets Layer) is an application layer (Layer 7) cryptographic protocol that provides secure communications over the Internet for web browsing, e-mail, instant messaging, and other data traffic. SSL, which was originally developed by Netscape and released in 1996, later served as the foundation for the IETF standard—Transport Layer Security (TLS) protocol. Although SSL and TLS vary in some respects and are not interoperable, the protocol architecture largely remains the same. The primary objective of both protocols is to provide data privacy and data integrity, thereby providing secure communications between applications. By default, SSL uses TCP port 443.
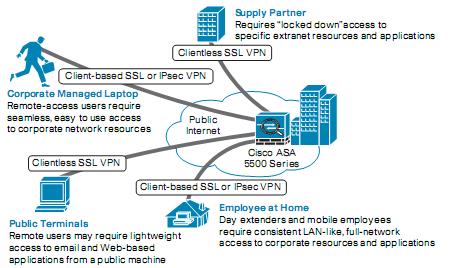
SSL VPN is an emerging technology offering a flexible, low-cost Internet-based remote solution by using the native SSL encryption of a web browser. SSL VPN does not require a special-purpose client software to be preinstalled on the system, thus enabling a user to connect from any computer, whether it is a company-managed or a non-company-managed system, such as a personal laptop, cybercaf, or home PC. SSL VPN sessions can be established from any Internet-enabled computer, thereby extending network access when and where required. SSL VPN use Secure Socket Layer (SSL) Protocol to create secure VPN. SSL is a Layer 7 crytographic protocol to provide secure communications over internet for web, email and other traffic. Almost all browsers support SSL protocol which makes SSL VPN a very strong and scalable Remote Access VPN solution. Thus SSL VPN is platform independent and can be used on a machine with any operating system which has a browser that supports SSL. An SSL VPN can be created from any machine that has an internet connection and a browser like Internet Cafes, Hotspots and of course company owned and personal computers where as IPSec Remote Access VPN are usually used by company managed desktops that have a client software installed.
An SSL VPN can be deployed using one of three access modes
- Clientless Mode (Layer 7): This mode provides secure access to web based applications only. It does not require any client software and runs from a web browser.
- Thin Client Mode (Layer 7): This mode is also known as port-forwarding and provides secure access to TCP based applications as well such as POP3, Telnet and SSH. A thin client is downloaded via Java Applet.
- Thick Client Mode (Tunneling): This mode provides network layer access to virtually any application over SSL VPN by downloading a SSL VPN Client Software from the VPN Server. This mode is usually used for company owned desktops
Figure below illustrates the different SSL VPN deployments.