Definition of ACL
An Access Control List or ACL is a list of authorizations that are attached to a specific object. These lists are used to specify the users or system processes that are allowed to have access to the objects. It also specifies which operations are allowed on specific objects. Every entry in the list specifies a subject and an operation.
In case of a network, the access control list is deployed at the router interface which then behaves in a specific manner based on the objectives of the list. The entire process has been charted in a flow-chart pattern for the ease of the user to understand router behavior implementing access control list.
Figure 1 below illustrates the behavior of a router that has an ACL configured on its interface.
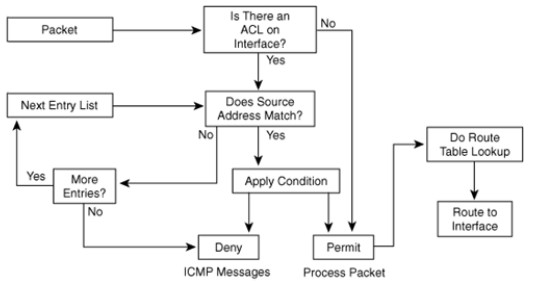
Figure 1: Behavior of a router that has an ACL configured on its interfaces
The above diagram is self explanatory since everything is given in the form of a sequel of events when an ACL exists. Basically as the packet arrives at the interface, it is either immediately permitted (in case there is no ACL) or is subject to a variety of checks such as address matching and so forth. After this loop completes successfully the packet is decided to be denied or granted permission, after which it is processed and is routed to interface.
The following functions are included in the ACL:
- Controlling the transmission of packets coming to and going out of the interface;
- Controlling virtual terminal line access;
- Restricting contents of routing updates;
- Define interesting traffic
Entries are made to the numbered ACE’s by following the pattern of one line at a time. The list is then scanned for a match in the same order. In case a change has to be incorporated the entire list has to be altered. The criteria of the ACL can be any of the following, the source address of the traffic, the destination address of the traffic, the upper layer protocol.
Where to Configure Access Lists?
For gaining the maximum benefits of this provision, it is necessary that ACL’s be configured on border routers. These are routers that are placed at the edges of the networks. This acts as a buffer from the outside network or even from areas within the network over which the control is much less. ACL’s can be configured in a way that inbound and outbound traffic both are filtered on an interface. ACL’s must be defined for every protocol on the interface for which the traffic is desired to be controlled.
Types of IP ACLs
The following types of ACL’s for IP are supported by Cisco IOS Software:
- Standard IP ACL’s: This type of list uses source addresses for performing matching operations.
- Extended IP ACL’s: This type of list uses source and destination addresses for carrying out matching operations. .
- Reflexive ACL’s: This type of list allows IP packets to be filtered based on session information. These lists contain information in the form of temporary entries and are nested within an extended, named IP ACLs.
Creation of an Access Control List
While creating an access list, the first step is to specify the protocol to filter. After this is done a name or a number is assigned to the access list. Multiple filtering criteria statements may be configured for a single access list. While configuring each access list must be uniquely identified within a protocol. This can be done by either assigning a name or a number to the protocol list. It would depend on the type of protocol that the list would be identified by a number or a name. Some lists are capable of being identified by either. While using numbers care has to be taken that the number falls within the specified range.
Table 1: Showing Protocol and Range
The primary things against which one should watch out while crafting access lists on Cisco routers are as under:
- The order in which you enter criteria;
- The implied deny all traffic criteria;
- Applying access lists to interfaces;
- Creating and editing access list statements on a TFTP server.
The Order in Which You Enter Criteria
Every additional list that is added gets appended to the end of the access list statements. It is not possible to delete an individual statement after it has been added. The entire list has to be deleted, modified and re-entered. The order in which the lists are entered is a matter of utmost importance. When the router has to make decision regarding which packets to forward or block the Cisco IOS software tests the packet against each criteria statement in the order in which the statements were created. It is only after a match is found that no more criteria statements are checked. This also means that if a criteria statement is given explicitly permitting all traffic, it will exclude all statements from being checked. If additional statements have to be added, the access list must be deleted and retyped with new entries.
Deny All Traffic
At the end of every access list is the deny all criteria statement. It is an implied criteria statement. The packet will be blocked in case it does not match any of the criteria statements. In the case of maximum protocols, when an inbound access list is defined for traffic filtering, it should also include an explicit access list criteria statements permitting routing updates. In case this is not done effective communication from the interface may be lost. This may happen due to the implicit deny all traffic statement, which is inadvertently present at the end of every access list.
Applying Access Lists to Interfaces
For certain protocols two access lists can be applied on an interface. One of the list is an inbound access list and the second an outbound access list. With all other protocols only one access list can be applied. The list checks both inbound and outbound packets.
In case of an inbound access list, the process that is followed is – the router receives the packet, the Cisco IOS software checks the access list for the criteria statement. In case a match is found the packet is permitted and the software continues with the processing of the packet. In the other case when the packet does not match the software discards the packet.
In case the access list is outbound, the process that is followed is – a packet is received and routed to the outbound interface; it is checked by the software interface for a match to the criteria statement. If the criteria matches, the packet is transmitted, and in case the criteria does not match the software drops the package.
ACL on Trivial File Transfer Protocol Server
The order of access list criteria statements plays an important role, as the lists cannot be reordered or deleted. It is always recommended by Cisco that all access list statements be created on a Trivial File Transfer Protocol servers. The entire list should be downloaded on the router after that.
For using a TFTP server, the access list can be created by using any text editor and then the same be saved in ASCII format. The TFTP server on which the lit is created should be accessible by the router. Use the command given below to copy ACL to the router
copy tftp:file_id system:running-config
After that use the below given command to save ACL in the NVRAM of the router
copysystem:running-config nvram:startup-config
In case changes are required to be made to an access list, the same can be done on the TFTP server and copy the edited file to the router as per the procedure discussed earlier.
As the first command of an edited access list issue a command that deletes the earlier access list. In case this is not done the new list will get appended to the previously existing access list.
Control for Both Ways
Since traffic could either be incoming or outgoing at an interface, it might be necessary to deploy two separate ACLs for incoming as well as outgoing traffic. Of course in certain protocols only one access control list would suffice. Depending on the situation packets which are either incoming or going are checked against the ACL and denied or permitted as the case may be. Another point worth noting in case of access control lists is that these do not filter packets which originate on the same router where these lists are applied.
