Definition of Firewall
A firewall denotes the set of related programs which are situated between a private network and external networks. It is normally located at the network’s gateway server and helps protect the resources of a private network. The term can also denote security policy. It can take on different forms while doing its job of blocking unauthorized and unwanted traffic from entry into a protected system. A firewall can be a specialized software program or a specialized hardware or physical device. It could also be a combination of both. Examples of these are Zone Alarm which is a software only firewall and Linksys, hardware firewall.
Firewall technology came to the fore in the late 1980s. The first generation of technology consisted of packet filters. The second generation started with application layers and the third generation had “stateful” filters. So important is the technology that is study is compulsory for the CCNA Security exam.
Cisco IOS Firewall Overview
The Cisco IOS Firewall set provides network security with integrated, inline security solutions. The Cisco IOS Firewall set is comprised of a suite of services that allow administrators to provision a single point of protection at the network perimeter. The Cisco IOS Firewall set is a Stateful inspection firewall engine with application-level inspection. This provides dynamic control to allow or deny traffic flows, thereby providing enhanced security. Stateful inspection will be described in detail later in this chapter.
In its most basic form, the principal function of any firewall is to filter and monitor traffic. Cisco IOS routers can be configured with the IOS Firewall feature set in the following scenarios:
- As a firewall router facing the Internet
- As a firewall router to protect the internal network from external networks, e.g. partners
- As a firewall router between groups of networks in the internal network
- As a firewall router that provides secure connection to remote offices or branches
The Cisco IOS Firewall provides an extensive set of security features that allow administrators to design customized security solutions to tailor to the specific needs of their organization. The Cisco IOS Firewall is comprised of the following functions and technologies:
- Cisco IOS Stateful Packet Inspection
- Context-Based Access Control
- Intrusion Prevention System
- Authentication Proxy
- Port-to-Application Mapping
- Network Address Translation
- Zone-Based Policy Firewall
Cisco IOS Stateful Packet Inspection
Cisco IOS Stateful Packet Inspection, or SPI, provides firewall capabilities designed to protect networks against unauthorized traffic and to control legitimate business-critical data. Cisco IOS SPI maintains state information and counters of connections, as well as the total connection rate through the firewall and intrusion prevention software. Stateful Packet Inspection will be described in detail later in this chapter.
Context-Based Access Control
Context-Based Access Control, or CBAC, is a Stateful inspection firewall engine that provides dynamic traffic filtering capabilities. CBAC, which is also known as the Classic Firewall, will be described in detail later in this chapter.
Intrusion Prevention System
The Cisco IOS Intrusion Prevention System, or IPS, is an inline intrusion detection and prevention sensor that scans packets and sessions flowing through the router to identify any of the Cisco IPS signatures that protect the network from internal and external threats. Cisco IPS solutions will be described in detail in the following chapter.
Authentication Proxy
The Authentication Proxy feature, also known as Proxy Authentication, allows administrators to enforce security policy on a per-user basis. With this feature, administrators can authenticate and authorize users on a per-user policy with access control customized to an individual level. Authentication Proxy configuration and detailed knowledge is beyond the scope of the IINS course requirements and will not be described in detail in this guide.
Port-to-Application Mapping
Port-to-Application Mapping, or PAM, allows administrators to customize TCP or UDP ports numbers for network services or applications to non-standard ports. For example, administrators could use PAM to configure standard HTTP traffic, which uses TCP port 80 by default, to use TCP port 8080. PAM is also used by CBAC, which uses this information to examine non-standard Application Layer protocols. PAM configuration and detailed knowledge is beyond the scope of the IINS course requirements and will not be described in detail in this guide.
Network Address Translation
Network Address Translation, or NAT, is used to hide internal addresses, which are typically private address (i.e. RFC 1918 addresses) from networks that are external to the firewall. The primary purpose of NAT is address conservation for networks that use RFC 1918 addressing due to the shortage of globally routable IP (i.e. public) address space. NAT provides a lower level of security by hiding the internal network from the outside world. NAT configuration and detailed knowledge is beyond the scope of the IINS course requirements and will not be described in detail in this guide.
Zone-Based Policy Firewall
Zone-Based Policy Firewall, or ZPF, is a new Cisco IOS Firewall feature designed to replace and address some of the limitations of CBAC, the Classic Firewall. ZPF allows Stateful inspection to be applied on a zone-based model, which provides greater granularity, flexibility, scalability, and ease-of-use over the Classic Firewall. ZPF is described in detail later in this chapter.
Uses of Firewalls
The term firewall comes from the construction industry and can be applied in many ways. To name a few scenarios for firewall use.
- Can automatically encrypt data sent over an organization’s network when it is spread over multiple physical locations. This results in the internet being used a private wide area network by the process of creating a VPN or Virtual Private Network.
- Can monitor, listen in and store all communications that flow to and from an external and an internal network. Endpoints and amounts of data received and sent, network penetrations and even internal subversion can be checked.
- Can aid in access control. A firewall can be used for blocking or controlling access to particular sites. It could also be used to bar users or machines from gaining ingress into other servers or services.
- Can be a good defense strategy to protect internal data and networks.
Strengths and weaknesses of a Firewall
While a firewall is an integral part of an organization’s security architecture and plays a vital role in protection of assets, it has strengths and weaknesses too. The strengths and drawbacks of a firewall are a must to know for anyone learning for CCNA 640-553 exam topic.
The strengths of a firewall:
- Helping to enforce security and safety policies of an organization.
- Restricting access to specified services. Access can even be granted selectively based on authentication functionality.
- Their singularity of purpose which means that companies need not make any compromises between usability and security.
- Its appraisal capacity which results in an organization getting to know and monitor all the traffic that sifts through their networks.
- Being a notification system which can alert people concerned about specific events.
The weaknesses of a firewall:
- An inability to fend off attacks from within the system that it is meant to protect. This could take the form of people granting unauthorized access to other users within the network or social engineering assaults or even an authorized user intent on malafide use of the network.
- It can only stop the intrusions from the traffic that actually passes through them.
- It cannot circumvent poorly structured security policies or bad administrative practices. For instance, if a company has a very loosely knit policy on security and over-permissive rules, then a firewall cannot protect data or the network.
- As long as a communication or transaction has been permitted, a firewall has no ability to protect the system against it. For instance, if a firewall has been built to allow emails to come through, it cannot detect a virus or a Trojan within that email.
Different Technologies of a Firewall and their strengths and weaknesses:
We can look at two main technologies of a firewall pertaining to CCNA 640-553 exam exam.
-
- Firewall Technologies based on Software
- Firewall Technologies based on Hardware
Software Firewall
These are very popular among individual home users. Like any other software, a firewall here is installed on the computer and can be customized according to the user’s needs. Most often, such a firewall is used for protecting one’s computer from outside attempts to access or use its data, can also provide protection against common Trojans or email worms. Many such firewalls also allow the user to define and set controls for establishing file sharing and printer sharing protocol. It could also keep out unsafe applications from running on your computer. There are two types of software based firewalls – rule based and non rule based. Examples of software firewalls are Zone Alarm, Kerio and Norton Personal Firewall. To put it simply, an effective way to choose and use a software firewall is to opt for a system that uses a small amount of resources on the computer and keep it updated with regular updates.
Strengths of a software firewall:
- Ideal for home or personal use.
- Very easy to configure and reconfigure with no requirement of specialised skills.
- Less expensive to buy.
- Easier to install and upgrade especially in comparison with hardware routers. The levels of security can be set with a few simple clicks of the mouse during installation.
- Flexibility – they allow the specification of applications that will be allowed to connect with the internet.
- Mobility – a software firewall moves with the computer regardless of the location it is on.
Weaknesses of a software firewall:
- May slow down system applications since it is installed on the system itself and requires more memory and disk space.
- May also prove costly because such a firewall has to be purchased separately for each computer on the network.
- It maybe unwieldy to remove from the system.
- Such firewalls cannot be configured to mask IP addresses. They only close unused ports and monitor traffic to and from open ports.
- May not be capable of fast reaction.
Hardware Firewall
A hardware firewall is amalgamated with the router that operates between a computer and an internet modem. While they can be purchased as a standalone product also, typically they are found in broadband routers. Normally they use packet filtering to check out where the incoming information is coming from, their destination addresses and if such traffic is related to an outgoing connection for eg, a request for a website. For effective use of such a firewall it is necessary to learn about their specific features, enabling them and testing for their efficacy from time to time. Some examples of such firewall are Cisco PIX, SonicWall, NetScreen and Symantec’s 5400 series applications.
Strengths of a hardware firewall:
- A single such firewall can provide protection for an entire network regardless of multiple computers.
- They work independent of system performance and speed since they are not situated on computers.
- They are more effective when companies use broadband internet connections like DSL or cable modem.
- It is less prone to malicious software.
- They are tailored for swift response and can handle more traffic load.
- Since it has its own operating system, it is less prone to attacks. They also have enhanced security controls.
- Ease of maintenance since a hardware firewall is typically situated in a standalone box, it is easier to disconnect or shutdown the box and minimize interference or downtime to the rest of the system.
Weaknesses of a hardware firewall:
- They treat outgoing traffic as safe and may fail if a malware is attempting to connect to the internet from within.
- They may be more complex to configure.
- They are more expensive.
- Takes up more physical space with its added wiring.
Best Practices for Firewall Implementation
In context of the Cisco certification for CCNA Security 640-553 exam, the best practices which need to be followed to have a maximum possible secure network is as follows:
- The network security policy should be build keeping in mind that no-one is fully trustworthy including any insiders or outsiders. This may not seem to be a very good idea from the humane perspective but needs to be adopted and implemented in security policy.
- Only the minimum number of personnel should be actually interacting with the firewall software and hardware, who are absolutely necessary to run the applications and maintain the physical appliances.
- Even their access should be strictly controlled and monitored. Every other activity should also be logged and monitored continuously. All alerts should be examined.
- Firewall stations should never be used for other routine applications such as servers or user work stations.
- All hardware and software in the firewalls should be up to date without leaving any room for a potential threat to sneak in.
Implementing a Firewall
It is all very well to study about the theory of the firewalls but it is time now to take a look at the internal nitty-gritty of the actual implementation of the firewall which will be helpful in your Cisco security certification, specifically the CCNA 640-554 exam topic.
Basically the firewall can be implemented using one of the four methodologies namely:
- IOS using CCP
- PIX technology
- Cisco Firewall Services Module
- Cisco Adaptive Security Appliance
It is the first method that we will consider in this tutorial and the main advantage of this method is that it does not require the use of any specialized firewall appliance but the normal Cisco router platform can be used to configure the same as a firewall using the Internetwork Operating System of Cisco.
Basically this method uses the inbuilt packet filtering technology of the Cisco IOS which is present in almost all routers, to act as a firewall. The main features which are implemented in Cisco IOS firewalls are stateful inspection, URL inspection, Intrusion detection and appliance awareness. We will study some useful commands related to these feature setups.
First the ip inspect command. This command is used to configure firewall inspection rule such as the following line:
Router(config)#ip inspect name firewall tcp
Once the rule is configured, it needs to be applied to an interface and the following command is used to apply the above configured rule. Remember to switch to an interface first.
Router(config)#interface e0
Router(config-if)#ip inspect firewall in
The next step is to create an access list which is important since the firewall working is based on traffic inspection and building up of a state table based on this inspection. We initially deny any incoming traffic entering from the interface using the following commands.
Router(config-if)#exit
Router(config)#access- list 100 deny ip any any
Then we can apply this inbound on an external interface using this command:
Router(config)#interface s0
Router(config-if)#ip access- group 100 in
The above is a simple example which shows the utility of inherent characteristics of the IOS to act as a packet filtering firewall. This type of features can be implemented using a wide range of Cisco router product families including but not limited to 800, 1700, 1800, 3600 and 7300 families. This gives a wide range of options to the users since these devices are widely used in all sorts of networks for core routing purposes.
In order to use the configuration wizard the following steps must be followed.
Make sure that the network configurations are complete and the IOS of the router being used is compatible for configuration of the firewall.
When the configuration wizard is launched, you can select the options amongst the BASIC & ADVANCED firewall configurations.
If the BASIC option is selected, the wizard uses the default access and inspection rules to create the firewall. This option is useful when there is only one outside interface and moreover the user is not interested to configure the DMZ network.
If the ADVANCED option is selected then the wizard asks the user to select amongst a variety of options relating to inspection and access rules and setup the firewall in a more customized manner. This helps the user to configure the DMZ network as well and is more suitable for situations where there is more than one internal and external interface.
It is worthwhile to note here that internal interfaces refer to those which are connected to the Local Area Network whilst the external interfaces refer to those connected to the Wide Area Network of the organisation under consideration. Moreover the DMZ refers to a demilitarized zone or is a buffer zone which is used to segregate traffic coming from outside sources which may not be trustworthy.
To configure the DMZ you need to specify the IP addresses for start and end, and the name and type of service to be configured such as say for example TCP, UDP etc.
The security policies which can configured for the CCNA 640-554 exam consist of a number of levels of Cisco security and each level as pre-defined settings. These levels could be either of these
- SDM_HIGH
- SDM_MEDIUM
- SDM_LOW
Furthermore the configurations of domain name and URL need to be set at the required parameters. The following is an set of example commands which are used to set the parameters for a trusted inside interface and the security policy to SDM_HIGH level.
Inside (trusted) Interfaces:
FastEthernet0/0 (10.28.54.205)
Apply access rule to the inbound direction to deny spoofing traffic.
Apply access rule to the inbound direction to deny traffic sourced
From broadcast, local loop back address.
Apply access rule to the inbound direction to permit all other traffic.
Apply application security policy SDM_HIGH to the inbound direction.
Intrusion Prevention System Lab Topology
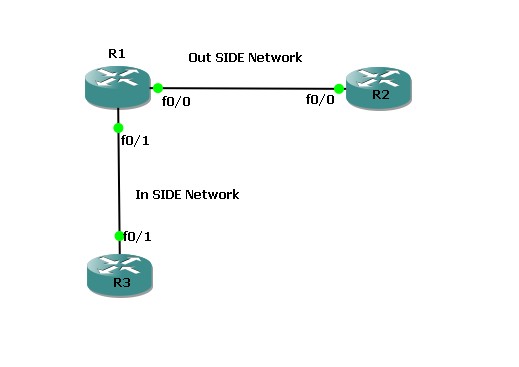
Lab Setup
- Make the connection as per the scenario.
- Use the IP addressing chart below to assign IP address to the routers.
- All three routers are configured with RIPv2. And can ping each other.
IP Addressing Schema
|
Router |
Interface |
IP Address |
|
R1 |
F0/0 |
100.1.12.1/24 |
|
F0/1 |
100.1.13.1/24 |
|
|
R2 |
F0/0 |
100.1.12.2/24 |
|
R3 |
F0/1 |
100.1.13.3/24 |
Lab Objectives
- Configure R1 to perform a generic TCP, UDP and ICMP inspection. Make sure that only the traffic that was initiated from inside is allowed back in. You should also allow the appropriate traffic through.
Configure R1 for TCP, UDP and ICMP Inspection
R1(config)#access-list 100 permit udp any any eq 520 (ACL permits the UDP traffic of RIP)
R1(config)#access-list 100 deny ip any any log (Deny to generated log of UDP RIP Traffic)
R1(config)#ip inspect name FW tcp (Inspect the TCP traffic) R1(config)#ip inspect name FW udp (Inspect the UDP traffic) R1(config)#ip inspect name FW icmp (Inspect the ICMP traffic)
R1(config)#int fa 0/0
R1(config-if)#ip access-group 100 in (Apply the ACL to interface)
R1(config-if)#ip inspect FW out (Apply the inspection rule to interface)
Verification
- To see the sessions, Telnet from R3 to R1, After telnet type the below mentioned command you will see the output , Once telnet session terminate , established sessions will gone.
R1#show ip inspect sessions
- When you trying to telnet from R2 (Which is our outside network) you will get some log messages in R1, which looks like below.
And on R2 you will see the messages below.
- You can see the inspection configuration with this command below.
R1#show ip inspect config
- To see, where the inspection rule is applied use the show ip inspect interfaces command.
Conclusion
In this tutorial we studied about the firewall technology and various methodologies used in the same specifically relating to the exam topic 640-554 covered under the CCNA Security certification. We also learned about the concepts of Intrusion Detection and Intrusion Prevention and saw that Cisco produces various types of specialized devices to help in the cause of Intrusion Prevention. Finally a lab scenario was created and simulated to help you practise the real thing. I hope you enjoyed this experience and it also gave you valuable information which will help you out in your Cisco studies.
