Well enough of historical anecdotes, now let us get down straight to business and see about firewalls. In the technical sense and the networking parlance, a firewall refers to a system or an arrangement which is used to control the access policy between networks by establishing a trusted network boundary or a perimeter and controlling the passage of traffic through that perimeter.
The figure below shows a typical firewall and how it acts as a boundary protector between two networks namely a LAN and WAN as shown in this picture
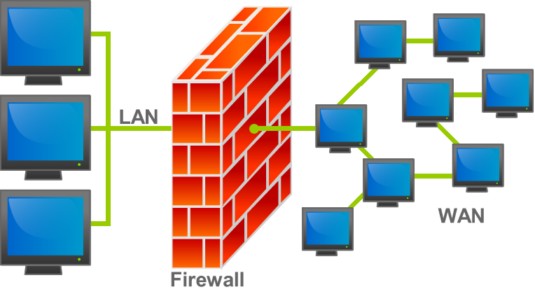
Firewall Visualization
There are certain features which are common to all types of firewalls including stateful firewall and some of these features are as follows.
- It is used for implementing and enforcing the policy regarding access to a network or the access control policy
- It is necessary for the entire traffic between the networks under consideration to pass through the firewall itself; it being the only point of ingress and egress. It would be really difficult to ensure complete security if there is any other point of entry or exit of traffic as that would act as a backdoor for attack
- The firewall should be hardened against all sorts of attacks since that is the only hope for the security of the network and hence it should be extremely difficult neigh impossible to compromise the security of the firewall itself, otherwise it would defeat the very purpose of having one in the first place.
- Firewalls act as points where the full strength of security can be concentrated upon without having to worry about every point. It is comparable to the border of a country where full military vigilance and strength is deployed on the borders and the rest of the nation is secure as a result of the same.
- However the above point could also act to the disadvantage for any fault or flaw in the firewall could expose the entire network to risk because that was acting as the sole point of security and barrier to attacks.
In context of Cisco networks the firewalls act to provide perimeter security, communications security, core network security and end point security. Also Cisco recognizes different types of firewalls such as static, dynamic and so forth.
In this tutorial we are going to concentrate on one particular type of firewall namely stateful firewall so let us take a look at what is meant by such a firewall.
A stateful firewall refers to that firewall which keeps a track of the state of the network connections traveling across it, hence the nomenclature. The programming of the firewall is configured in such a manner that only legible packets are allowed to be transmitted across it, whilst the others are not allowed.
This stateful inspection in the firewall occurs at layers 3 and 4 of the OSI model and is an advanced technology in firewall filtering. In order to achieve this objective, the firewall maintains a state table of the internal structure of the firewall. Whenever a packet is to be sent across the firewall, the information of state stored in the state table is used to either allow or deny passage of that packet.
Take a look at the figure below to see and understand the working of a stateful firewall.
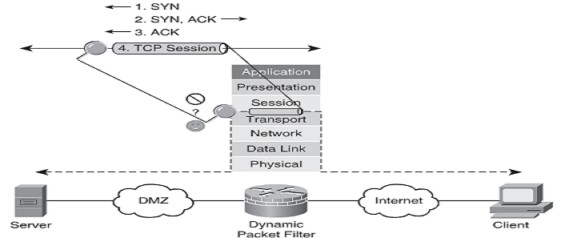
Stateful Firewall Operation
In the below scenario we will examine the stateful firewall operations and functions of the state table using a lab scenario which is enlisted in full detail in the following sections. You can see that how filtering occurs at layers 3 and 4 and also that the packets are examined as a part of the TCP session.
The topmost part of the diagram shows the three-way handshake which takes places prior to the commencement of the session and it is explained as follows
- Syn refers to the initial synchronization packet sent from one host to the other, in this case the client to the server
- The server sends acknowledgement of the syn and this known as syn-ack
- The client again sends acknowledgement of this syn-ack thereby completing the process and initiation of TCP session
- Either of the two parties can end the connection at any time by sending a FIN to the other side. This is something similar to a telephone call where either the caller or the receiver could hang up
The State Table
We have been referring to the stateful firewall and that it maintains the state of connections, so a very important point to be discussed in this regard is the state table.
The procedure described previously for establishing a connection is repeated for several connections. The information related to the state of each connection is stored in a database and this table is referred to as the state table.
So whenever a packet arrives at a firewall to seek permission to pass through it, the firewall checks from its state table if there is an active connection between the two points of source and destination of that packet. The end points are identified by something known as sockets.
A socket is similar to an electrical socket at your home which you use to plug in your appliances into the wall. Similar a network socket consists of a unique IP address and a port number and is used to plug in one network device to the other.
The packet flags are matched against the state of the connection to which is belongs and it is allowed or denied based on that. Take for example where a connection already exists and the packet is a Syn packet, then it needs to be denied since syn is only required at the beginning.
Security features
Let us study some of the features of stateful firewalls both in terms of advantages as well as drawbacks of the same.
- Stateful firewalls are active and intelligent defense mechanisms as compared to static firewalls which are dumb. A stateful firewall just needs to be configured for one direction while it automatically establishes itself for reverse flow of traffic as well.
- Attacks such as denial of service and spoofing are easily safeguarded using this intelligent safety mechanism.
- However stateful filtering occurs at lower layers of the OSI model namely 3 and 4, hence application layer is not protected. Moreover functions occurring at these higher layers e.g. authentication of users to connections cannot be done because of the same reason
- All protocols and applications cannot be handled by stateful inspection such as UDP, FTP etc because of their incompatibility with the principle of operation of such firewalls. For example some applications may be using dynamic ports.
