An IDS works based on the principle of analyzing copies of the data that is flowing rather than analyzing the actual data and hence does not obstruct the flow of traffic, or in other words it does an offline analysis of the data.
An IPS on the other hand monitors all data between layers 2 to 7 of the OSI model in real time by actually making the traffic to flow through it and can actually stop malicious traffic from entering or leaving the network.
The actual implementation of the IDS/IPS can be done using either hardware or software or combination of both. Basically intrusion detection and prevention systems can be deployed in two places namely
- In the Host
- In the Network
The former is known as HIPS (or HIDS as the case may be) whilst the latter is Network IPS or Network IDS. The differentiation is mainly based on the fact whether the IDS/IPS looks for attack signatures in the log files of the host or the network traffic. Network IDS takes raw network data packets as source for its investigation and analyzes them in real time to find out the malicious traffic, as compared to HIPS which works by analyzing log files for suspicious activity.
Of course each of these technologies have their own strengths and weak points, and it is always better in a practical situation to use a proper mix of these technologies to achieve an optimum level of security from attacks for the network. Let us now study these systems in detail from a generic point of view as well as from the point of view of the Cisco security certification viewpoint.
Host based systems
As already studied, a host based systems protects a unique host by attaching itself closely to the operating system kernel and forming a layer which filters all system calls as well as application call and allows only call which are legitimate to go through. There can be four types of host based instruction detection systems namely
File system monitors: this implementation of HIDS works by comparing the files present in the system with previous version of the same file to check for any unauthorized changes. These changes can be in content, size, modification date and so forth. This would give a clue if any file or directory seems to be tampered without the authorized users express permission. Sometimes hashing algorithms can be deployed to verify the check sums for these file sand directories which would give an indication of any change which was not supposed to be there.
There could be many loopholes which could give way to the attacker in such a file based monitoring system. Say for example that sometimes the temporary files are not subject to such checks since their content changes too much – too often. This could give a sort of backdoor to the intruder for carrying out intrusion attempts. Similarly any collision in the hashing algorithms could act as entry point for intruders.
Logfile analysis: analyzing the log files as a means to detect any possible intrusion attempts and as warning signal for administrators is another method of carrying out host based protection. There are several tools and applications which help in such analysis. Basically these tools work by observing and analyzing patterns of behaviour which are then correlated to events that have occurred in the past or defy normal behavioural norms.
Connection analysis: these types of HIDS systems work by analyzing network connections that are made to a host and thereby trying to guess which are authorized while which of those are malicious and an attempt to intrude. These can be portscan attempts, unauthorized TCP connections and so forth
Kernel based detection: in this method the kernel itself detects intrusion attempts as it is modified to do so. This is achieved by logging changes to system binaries, anomaly in system calls and so on.
Cisco Security Agent or CSA refers to the intrusion prevention system which is provided by Cisco for HIPS implementation. Originally this system was developed by a company named StormWatch but has been acquired by Cisco Systems more than half a decade ago. CSA is the Cisco’s answer to host based intrusion detection and prevention and some of the features offered by CSA are as follows:
- CSA does not require any specialized hardware appliance to be implemented which is certainly a great advantage.
- Being a host based system, CSA needs to be deployed on each host that needs to be protected on the network which is an obvious corollary of HIPS
- It works in all the modes described above for intrusion detection systems since it logs files, analyzes system calls, registry changes and so forth
- CSA also acts based on behavioural patterns and so any abnormal behaviour patterns which are identified by these systems can be subject to denial even if those attacks are not present on the list of predefined attacks. This way it acts as anomaly based detection system as well.
The main advantage of using a host based prevention system is that since the protection system is integrated with the host itself, it is very easy to point out whether the actual attack has been successful or not. This is a very vital piece of information which is not easily obtained in the network based protection mode. Also it is very difficult for a hacker to get past the host based protection system by using fragmentation attacks.
One of the obvious disadvantages of a host based attack prevention system is the large number of hosts on which the instance of the CSA must be implemented in order to prevent any possible attempts of intrusion. Since could be a very cumbersome process on a huge network which might have thousands of hosts. Obviously the best bet in such a case is to use a judicious combination of host and network based protection systems, with the host version only used on critical points of the network, whilst the rest are covered under the network based protection system.
Since the host based intrusion prevention system is defending only a specific host, it is certainly at a disadvantage when it comes to the bigger picture of the entire network. This means that the HIPS is blissfully oblivious of the happenings on the network. Take an imaginary situation in which the entire network has been ransacked by intrusion except perhaps a couple of hosts. The HIPS of those host would not be aware of such a situation and this could be dangerous position to be in at any point of time.
Similarly if the network has a large number of hosts and most of them use different types of operating systems, it might be difficult to deploy a specific host based protection system because it might not be compatible with all types of OS. In this case there might be a need to configure different HIPS on different hosts which in turn could lead to heterogeneity and different levels of security.
Network Based Protection
Take a look at the figure given below which shows a network based protection scenario as compared to the host based method discussed earlier. As you can see that there is a protection system in place at the entrance of the protected network which gives combined protection to the different types of hosts in one go. This is known as the network based intrusion prevention system.
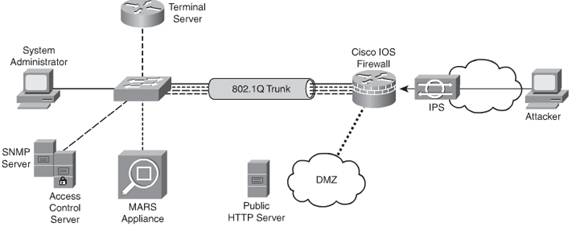
Network Based Intrusion Prevention System
As you can make out in the figure above, this system qualifies as an intrusion prevention system mainly because it is in line to the traffic flow rather than analyzing copies of traffic (remember your basics of IPS vs IDS you learnt in another tutorial). The above prevention system is deployed on the WAN side of the Cisco IOS firewall whilst the other half of the LAN side is taken care of by the firewall itself.
Let us take a look at some of the common features of such network based protection systems.
- A main plus point of these types of systems is that they are easy to deploy and cost effective since a single device is capable of protecting the entire network or at least its certain segments as compared to host based systems which require as many instances of the system as the number of systems to be protected.
- Because of this very reason, these systems are easily scalable since addition or deletion of new hosts in the network does not necessarily mean increasing the hardware and so forth. Even if new appliances have to be added, they are relatively easier to install and configure
- This also means that the hardware and the operating system can be hardened for providing the best possible level of security
- Concentrating on one point of security is easier than concentrating on hundreds or thousands of protection points at every host in the network.
- Due to being deployed at the network level and not individual level hosts, it is not possible to check for a successful attack in NIPS mode.
- Yet it is possible to see lower level network events which are occurring and this information could be vital at times. Please note that it is not possible to view such events whilst using HIPS or HIDS mode
- It is not possible to check out data streams which are encrypted using network protection mode, which is obviously a substantial disadvantage.
Some of the popular Cisco devices used for intrusion prevention systems include but not limited to the following
- Cisco 4200 Series Sensors
- Cisco ASA 5520 with AIP-SSM-20
- Cisco IDSM-2 Module for Catalyst 6500 Series Switch
- Inbuilt IOS IPS features can be enabled using devices such as Cisco 800 Integrated Service series
Now let us study a lab scenario in this context.
Scenario: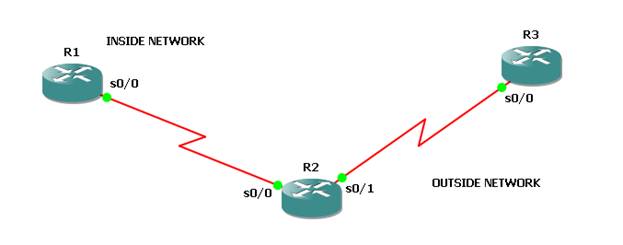
Lab Setup
- Make the connection as per the scenario.
- Use the IP addressing chart below to assign IP address to the routers.
- All three routers are configured with RIPv2. And can ping each other.
IP Addressing:
Router |
Interface |
IP Address |
|
R1 |
S0/0 |
100.1.12.1/24 |
|
Loop0 |
1.1.1.1/24 |
|
|
R2 |
S0/0 |
100.1.12.2/24 |
|
|
S0/1 |
100.1.23.2/24 |
|
|
Loop0 |
2.2.2.2/24 |
|
R3 |
S0/0 |
100.1.23.3/24 |
|
|
Loop0 |
3.3.3.3/24 |
Lab Objectives:
- Configure R2, that only Allow the following traffic through its S0/1(Outside Network) interface:
- SMTP traffic that originates from the inside networks
- Only Java applets from network 1.1.1.0 /24 should be down loaded. Ensure that audit trail logging and real time alerts are enabled for this inspection.
- Net-meeting traffic that originates from the inside networks
- Routing traffic for RIPv2 and ICMP should function properly.
Lab Solution:
Solution 1
On R2
R2(config)#access-list 1 permit 1.1.1.0 0.0.0.255
R2(config)#access-list 100 permit icmp any any
R2(config)#access-list 100 permit udp any any eq rip
R2(config)#ip inspect name FIREWALL http java-list 1 alert on audit-trail on
R2(config)#ip inspect name FIREWALL smtp
R2(config)#ip inspect name FIREWALL h323
Note: – h323 protocol is used for MS NetMeeting, Intel Video Phone
R2(config)#int s0/1
R2(config-if)#ip inspect FIREWALL out
R2(config-if)#ip access-group 100 in
Key Point to Remember:
- The access-list for the Java applets must be standard.
- If the access-list does not exist, all Java applets from all address will be blocked.
- IOS Firewall does not detect or block encapsulated Java applets such as applets in “.zip” format.
- IOS Firewall does not detect or block applets loaded via FTP, Gopher or HTTP on a non-standard port.
By these key points we can think about the operational strengths and weaknesses of the IOS Firewall technologies
Verification: Interface Configuration R2#show ip inspect statistics
R2#show ip inspect all
Session audit trail is disabled
Session alert is enabled
one-minute (sampling period) thresholds are
max-incomplete sessions thresholds are [unlimited : unlimited]max-incomplete tcp connections per host is unlimited. Block-time 0 minute.
tcp synwait-time is 30 sec — tcp finwait-time is 5 sec
tcp idle-time is 3600 sec — udp idle-time is 30 sec
tcp reassembly queue length 16; timeout 5 sec; memory-limit 1024 kilo bytes
dns-timeout is 5 sec
Inspection Rule Configuration
Inspection name FIREWALL
http java-list 1 alert is on audit-trail is on timeout 3600
smtp max-data 20000000 alert is on audit-trail is off timeout 3600
h323 alert is on audit-trail is off timeout 3600
Interface Serial0/1
Inbound inspection rule is not set
Outgoing inspection rule is FIREWALL
http java-list 1 alert is on audit-trail is on timeout 3600
smtp max-data 20000000 alert is on audit-trail is off timeout 3600
h323 alert is on audit-trail is off timeout 3600
Inbound access list is 100
Outgoing access list is not set
Interfaces configured for inspection 1
Session creations since subsystem startup or last reset 0
Current session counts (estab/half-open/terminating) [0:0:0]Maxever session counts (estab/half-open/terminating) [0:0:0]Last session created never
Last statistic reset never
Last session creation rate 0
Maxever session creation rate 0
Last half-open session total 0
TCP reassembly statistics
received 0 packets out-of-order; dropped 0
peak memory usage 0 KB; current usage: 0 KB
peak queue length 0
