These days the Ethernet switches have literally replaced the shared media hubs especially in the large corporations. The ability and usefulness of the Ethernet switch lies in its ability to memorize the MAC address of each of the ports connected to it, so that any frame which enters the switch, can be forwarded to the appropriate address. In case there is no address available for delivery, the frame can be stored in the MAC address table of the switch which also goes by the name of a CAM table. It is also important to note that many switches group a particular set of ports into virtual LANs or VLANs. Hence the basic security features of the switches need to be configured in order to prevent such a situation to occur.
Types of Attacks
Before learning about configuring switches for security improvements, let us take a look at some of the types of attacks to which these layer 2 switches are vulnerable as that would lay the foundation for studying further.
VLAN hopping attacks – This type of attack occurs when a switch is deliberately misled to hop or direct traffic from the genuine VLAN to which it is connected to another VLAN. This could be a dangerous situation since sometimes traffic within the VLANs could be without encryption and even sensitive information such as passwords could get revealed. Furthermore this type of attack could be carried out either using rogue trunk or double tagging.
In the rogue switch method, the hacker possibly gets attached to a switch on an unused port and uses the dynamic trunk protocol to negotiate trunking with another switch by spoofing DTP messages. In this way a VLAN gets compromised and traffic can be injected into that VLAN for malicious purposes.
The double tagging VLAN hopping attack is carried out based on the hardware functionality of switches. Since as a rule switches only unencapsulate the 802.1 Q frames, the hacker follows a policy of sending unicast of broadcast traffic to the switch. The trick lies in using a tagged 802.1Q frame within another layer of tagged frame. This means that the inner frames get carried over to various ports and trunks. All this is seen in the figure below
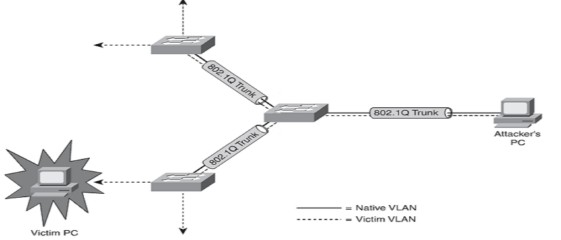
Double Tagging VLAN Hopping Attack
STP manipulation attack – This attack makes use of the spanning tree protocol and the attacker attaches to a port on the switch either directly or via another switch. The STP parameters are manipulated in order to achieve the status of a root bridge which helps the attacker to see various frames which otherwise would not be visible. I will not go into the technical details of the root bridge which you must have already studied, but if you recall about the BPDU or bridge protocol data units it will help you to understand this attack in a better manner. Each of these data units have an identification number known as bridge ID or BID. The BID in turn consists of bridge priority and the MAC address. If the attacker is able to inject BPDU frames whose bridge priority in the BID are lower than the already existing root bridge, it automatically becomes the root.
CAM table overflow method – CAM stands for content addressable memory and as you must be knowing it represents information regarding MAC addresses, the ports from where they can be reached and the associated VLAN IDs. The Ethernet packets that arrive at each port supply information regarding this from their headers. It is all very well organized except for the fact that even the latest switches can hold a few thousand such entries which could range from say around 4096 entries for 2900 series catalyst switches to several thousand in the higher version such as 6500 series. This obviously would have hinted how this attack works. Yes, you are right for the attacker now floods the switch with fake packets having fake MAC addresses. Since these addresses will now replace the limited space available in the CAM table, any further genuine unicast packets will get broadcasted instead of being unicast. This simply means that the attacker now needs to listen on any port and catch that genuine traffic thus compromising security.
MAC Spoofing – this is quite similar to the above except that instead of flooding the CAM table with fake MAC addresses, the MAC address of a genuine and existing host is used, which means that the answer to that will now go to the spoofed ID rather than the genuine ID. Of course this attack assumes that the genuine host is silent in the meantime for it if transmits during this period, it would lead to detection.
Catalyst Switch Security Features
After taking a look at some of the common types of attacks on layer 2 devices i.e. switches we will take a look at some of the security features and how to configure them in order to mitigate such possible attacks. You might be thinking that it would require some high techniques to mitigate the attacks described above. Well fortunately for all of us, this is not so and these attacks can be kept at bay by using basic security features which can be enabled easily. We will learn about the actual configuration of some of these features in the lab towards the end of the tutorial but first of all let us see some of these features and how they can be used to repel or discourage attacks.
Trunking – If you turn off trunking you cut out the way for attackers who are planning to initiate VLAN hopping attacks. Similar dynamic trunking protocol or DTP should be disabled on all ports and should only be manually enabled on ports at which it is required. Similarly keeping the navite VLAN different from user VLANs ensures that double tagging attack is avoided.
Portfast – This feature is used to put any port which is not a part of the spanning tree protocol calculations in the portfast mode, which ensures that the switch cannot put that interface in the blocking mode. State in simple terms it means that the attacker will not be able to exactly guess about the network topology and only have an idea about it, making the job of attacking more difficult if not impossible. The only precaution you need to take is to ensure that the interface is not a part of the topological loop before it is put into the portfast mode. Another method could be to put all interfaces in portfast mode and manually undo on required interfaces.
BPDU Guard – Previously we covered that BPDU frames can be deliberately used to elect a root bridge by an attacker, hence a method is used whereby an interface is blocked if it receives BPDU frames and this when used in conjunction with the Portfast feature described above, is very useful in preventing STP manipulation attacks.
Root Guard – This is a closely related activity to the above two and works by putting an interface in the listening mode whenever it receives a BPDU with a superior BID, and putting things back to normal when this superior BPDUs cease.
Port Security – There are several types of security features which could be set up on a port and help to avoid various types of common attacks described above. Say for example if you configure the port to learn a specific number of MAC addresses only, it would thwart any attempts of MAC spoofing and even CAM table overflow methods of attack. Similarly static MAC addresses can be assigned to a port and also specific actions can be programmed to be carried out if any violation from the norm occurs. An important point to remember in case of port features is that it requires you to enable port for access mode before the security features can be applied to it.
Intrusion Notification – We can consider sending notifications to the network management system or NMS using simple network management protocol or SNMP. Whenever some new dynamic MAC addressed is learned, it can send a notification and this features can be used in ultra secure environments where there should not be any attack or the attack could prove very costly either in monetary terms or loss of useful information like say from a military premises. The MAC address notification command can be used to configure this feature and it should be used with care to prevent unnecessary load on the network management system.
Switched Port Analyzer – This feature also known as SPAN is used for mirroring a port which is then used to analyze the traffic by copying it exactly (i.e. mirroring) and checking for anomalies without actually affecting traffic flow through the actual network, hence it is basically an intrusion detection system.
Strom Control – This feature is used to suppress unnecessary traffic and hence can be used to prevent denial of service attacks. Basically this feature is enabled and a limit is set for all types of traffic at a port including broadcast, multicast and unicast traffic. Any traffic over that range is simply dumped and thus saving the network from being attacked or overloaded. The threshold can be defined in various ways such as percentage of total bandwidth, packets per second or bits per second as may be convenient depending on the situation.
