As obvious, the two main characteristics of IPSec
Tunnel Vs Transport Mode
relate to authentication and encryption. Whereas authentication protects the private network and the data within that network, encryption tries to conceal that data so that it is not decipherable by any unauthorized personnel. The level of functioning of the IPSec is at the network layer of the OSI model and it can be used for a variety of functions including but not limited to the following:
- Packet filtering
- Authenticate traffic between two hosts
- Remote access over the Internet
- Enable communication between remote offices
Currently the standards used in Cisco for IPSec implementation are DES and 3DES, i.e. data encryption standard and tripe data encryption standards and they are used in the Cipher Block Chaining or CBC mode.
What is CBC?
If you are not aware of the CBC mode, let me tell you that it basically consists of a technique wherein the plain text is divided into blocks of 64 bits. Each of these blocks is then exclusive XORed with the previous ciphertext block on a bit by bit basis. Hence it results in unique encryption pattern for even similar blocks if present at different places. This means that several types of attacks are straight away avoided by using this technique as even the same block of plaintext would appear as different blocks of ciphertext if present at multiple places.
Of course it must be also added that despite this strength, CBC is not a foolproof mode and advanced cryptoanalysis techniques can be used to decipher or break the code.
DES and 3DES
When using DES standard with CBC mode, IPSec is implemented by generating a pseudorandom stream of bits which are then XORed to produce the subsequent ciphertext blocks. Hence obviously the keys need to be changed frequently to escape from advanced forms of brute force attack. Also since the chain is only as strong as its weakest link, it is best to use strong keys to generate strong ciphertext. Last but not least, the channel used for exchange of keys between the sender and the receiver also needs to be secure lest the keys are compromised during such exchange or transfer.
The technique used with triple DES is quite similar but the process is repeated 3 times (hence the name of the method) and this leads to a much secure ciphertext which isn’t that easily breakable as the normal DES CBC method.
Basically the technique consists of using three 56 bit keys and first encrypting the plain text, data is decrypted using the second key and finally it is again encrypted using the third 56 bit key. The reverse process is followed while deciphering this data and results effectively in a 168 bit key.
Advanced Encryption Standard
Another algorithm with the name of AES or advanced encryption standard is also being used and it does offer some security improvisations over the 3DES version, but since the latter has been in popular use since more than 3 decades, it will continued to be used for coming future. Cisco is already offering AES in several of its product lines including VPN appliances.
The SEAL
The SEAL encryption is another building block of IPSec which is extensively used in Cisco IOS devices. It puts lesser load on the CPU but this cipher has several limitations such as only being used by the Cisco Company and so forth. This certainly limits the application of the same, yet it is a useful algorithm.
Hashing
We learnt towards the beginning of this tutorial that data integrity is an important part of the IPSec functions. A useful technique to ensure data integrity is the hash function. Basically hashing consists of inputting a data of any length into a function and the output is always a fixed length hash. This fixed length is also known as the digest or fingerprint of that data. Mathematically speaking, hashes are very similar to the cyclic redundancy checks and are much more strong from the encryption point of view.
VPN Tunneling
With the advancements in technology, geographical distances have ceased to matter; to a great degree if not completely. Companies nowadays have most of their staff at different geographically dispersed locations. Yet effective communication and transfer of data between these sites is vital for the proper and efficient function of the organizations.
There are several methods of making such connections between these different sites and one of the cost effective methods is the use of broadband and DSL. But these media are highly risky since security can be a grave concern on such public networks such as the Internet. Hence a technique consists of creating virtual tunnels between the connecting sites wherein the data seemingly travels safety on a sort of private highway along the information super highway or the Internet. IPSec can be used for create VPNs or virtual private tunnels.
Security Features
There are lots of security features which are offered by IPSec in such site to site VPN connections and some of these are as follows.
- If the data happens to get intercepted by any unauthorized party, it would be useless for them if it cannot be read or understood by them. Hence confidentiality of the data is assured using IPSec and we have already studied in the previous sections about this.
- Data confidentiality is of not much use if the data starting from the sender end does not get reciprocated at the receiving end. Hence integrity of data is equally essential and several techniques are used to ensure that the data has not been modified deliberately during its transit.
- The last but equally important factor is that of authentication. It is of utmost importance to ensure that the data is received from the intended recipient only. For example if data is not stolen or modified during transition, it would serve no purpose if the parties involved in data exchange are not confirmed about the identity of each other. Hence this is another security feature which is provided by IPSec.
Now let us take a look at the two modes of operation of IPSec namely transport mode and the tunnel mode but before that it would be better for us to take a look at the different between security policy and security association.
Security Policy, as the name itself suggests is the policy about security or the rules that are programmed into the IPSec implementation. The datagrams are treated with respect to the security rules or policy.
A closely related concept is that of the Security Association, which is describes the secure connection between the devices. The information of the above two are stored in different databases known as the security policy database and security association database.
Now we revert to the discussion about the modes of IPSec operation as follows.
- The Tunnel Mode is mainly used to connect two gateways and/or a gateway to the end station, in which the other gateway acts like a proxy to that station behind it.
- Transport Mode on the other hand is used mainly between end stations or between the end station and a gateway. Hence you can see that when it comes to connecting an end station and a gateway, either of the two modes could be used.
Let us take a look at the associated picture which shows a PC on the left hand side and servers on the right side. In between, as the symbols suggest, there are routers and PIX firewall.
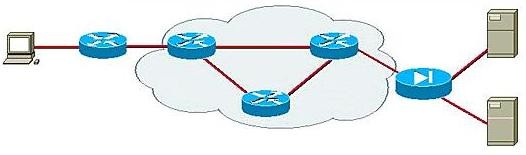
Tunnel Vs Transport Mode
When the PC user has to connect to the servers, it could be done either by using the tunnel mode or the transport mode.
- When both end terminals connect directly together, they form a transport mode of operation
- When the end station connects to IPSec gateway it is the tunnel mode.
Similarly several other configurations could exist in the same scenario. Can you identify some more of them? Another way of looking at this distinction is the difference of headers in both these modes of IPSec. The tunnel mode protects the entire datagram including headers and so forth, while it is not the case in transport mode.
The following figures depict the order of headers on both these cases
|
IP header |
IPSec Header |
IP Payload |
Transport Mode Headers
|
IP header (new) |
IPSec Headers |
IP header (old) |
IP Payload |
Tunnel Mode Headers
Is it so simple really?
It must also be noted that in actual practice, things are not so sweet and easy as they have been presented to you here. In the actual scenario there are other factors to be considered as well. One of these factors is the IP version while the other is the protocol being used.
So you can come to the conclusion that on the whole since the are three factors namely mode, protocol and version and there are two choices in each case, there would be 8 possible choices for any given combination of these mathematically speaking (remember the formula 2 * 2 * 2 = 8 choices)
If you are not aware about the two protocols being talked about let us discuss those as well. They are the AH and ESC protocols described as below.
AH or the authentication header protocol is exactly what its name suggests (how you wish every tech-term would be like that). It is used to identify the contents of a datagram with the help of a header which is created specifically based on those very contents it intends to verify.
ESP or encapsulating security payload protocol is used in situations where a relatively higher level of security is required which is not feasible using the AH protocol alone. Hence in such cases the datagram is encrypted using a key for transmission purposes. This way it can be ensured that not only does the packet come from where it is supposed to come, but also it has not been tampered on its way. The ESP field consists of 3 components namely
- Header (SPI, Sequence Number)
- Trailer (Padding, Pad Length)
- Authentication Data (Integrity Check Value)
IPSec Key Exchange
Let us finish this tutorial by learning something about the IPSec key exchange. You must already be familiar with the concept of exchanging keys securely. This is important since the keys are used to encrypt and decrypt messages using various algorithms, hence it is important that those keys itself are safe in the first place. Of course it does not mean to say that anyone with a key can read the data since EPS is meant to prevent exactly this kind of intervention, still the exchange of keys is an important step in the area.
In more technical language IPSec key exchange refers to the process of exchange of security associations between IPSec enabled devices. This information is then stored in their respective security association databases to be used later on. It is quite a complicated topic beyond the scope of this tutorial but it would be sufficient for you to know at this stage that it consists the combined features of 3 protocols as follows
- Internet Security Association and Key Exchange Management protocol
- SKEME
- OAKLEY
