Cisco CCNA Access List Applications
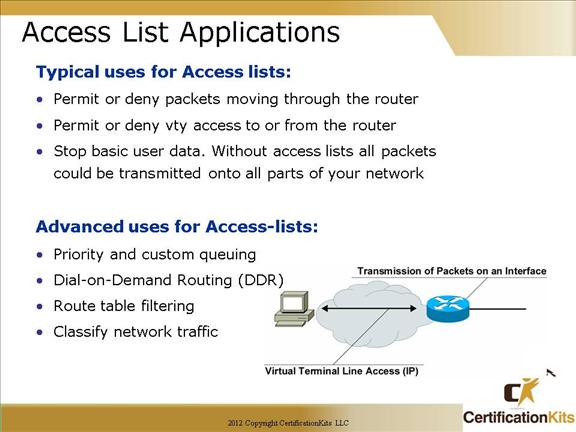
This slide illustrates common uses for IP access lists.
While this chapter focuses on IP access lists, the concept of access lists as mechanisms to control traffic in a network applies to all protocols.
An improved security solution is the lock-and-key access feature, which is available only with IP extended access lists. Lock-and-key access allows you to set up dynamic access lists that grant access per user to a specific source/destination host through a user authentication process. You can allow user access through a firewall dynamically, without compromising security restrictions.
Access lists can be used to permit or deny packets moving through the router, permit or deny Telnet (VTY) access to or from a router, and create dial-on-demand interesting traffic that triggers dialing to a remote location.
Cisco CCNA Wildcards Review
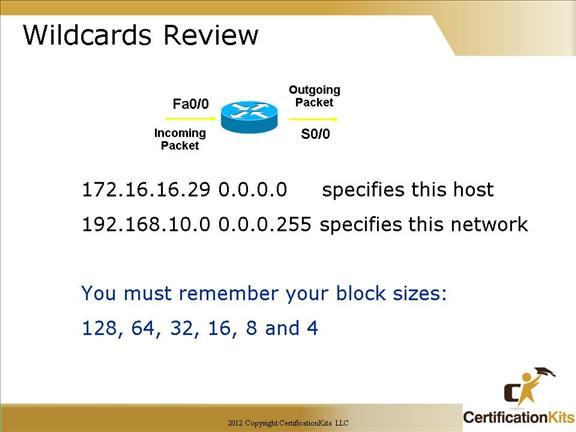
Wildcards are used with access lists to specify an individual host, a network, or a certain range of a network or networks.
To understand a wildcard, you need to understand what a block size is; they’re used to specify a range of addresses. Some of the different block sizes available are 64, 32, 16, 8, and 4.
Wildcards are essentially opposite of a subnet mask where a 0 in the bit position specifies an exact match while a 1 in the bit position specifies a wildcard. For example, a mask of 0.0.0.255 specifies the first three octet must match exactly while the last octet can be any value between 0 and 255.
Cisco CCNA Wildcard Masks
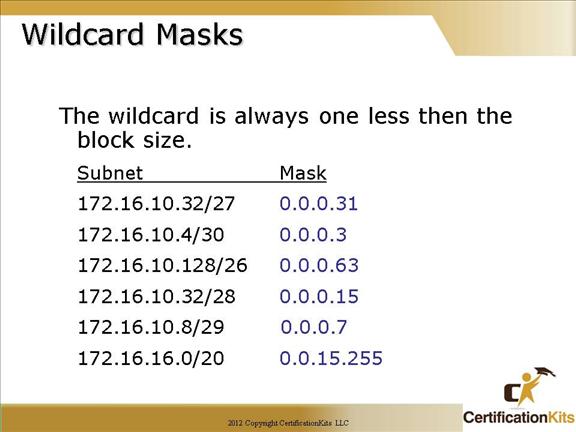
This is a review of wildcard masks, as first discussed when configuring OSPF.
You really need to know these!!
172.16.10.32/27 or 0.0.0.31 matches a last octet value between 32 and 63.
172.16.10.4/30 or 0.0.0.3 matches a last octet value between 4 and 7.
172.16.10.128/26 or 0.0.0.63 matches a last octet value between 128 and 191.
172.16.10.32/28 or 0.0.0.15 matches a last octet value between 32 and 47.
172.16.10.8/29 or 0.0.0.7 matches a last octet value between 8 and 15.
172.16.16.0/20 or 0.0.15.255 matches a third octet value between 16 and 31 and the last octet can be between 0 and 255.
Cisco CCNA Access List Command Overview

There are two steps required when implementing IP ACLs. First the ACL needs to be created which is done is global configuration mode. Secondly, the newly created ACL needs to be applied to an interface. The ACL can be applied to packets entering the router (in) or exiting the router (out). ACLs are created utilizing the access-list command while they are applied utilizing the ip access-group command.
The example demonstrates a “basic” standard access-list. Each of the three test statements accomplish the same thing. It is showing three different ways to specify a host entry.
Cisco CCNA Wildcard Example 1
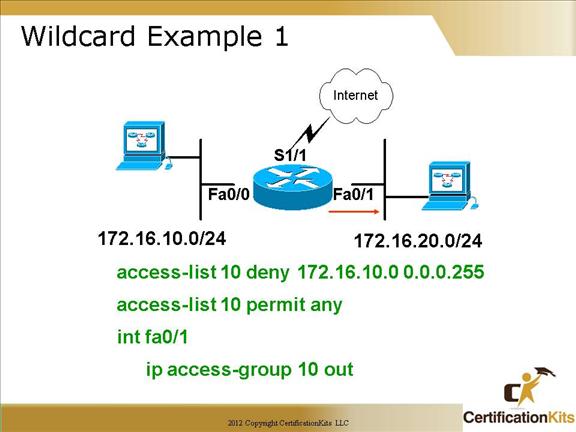
This example will deny host on network 172.16.10.0/24 (172.16.10.0 – 172.16.10.255) from exiting interface fa0/1. Note that it denies those addresses from exiting interface fa0/1 due to the ip access-group command being applied as out.
Cisco CCNA Wildcard Example 2
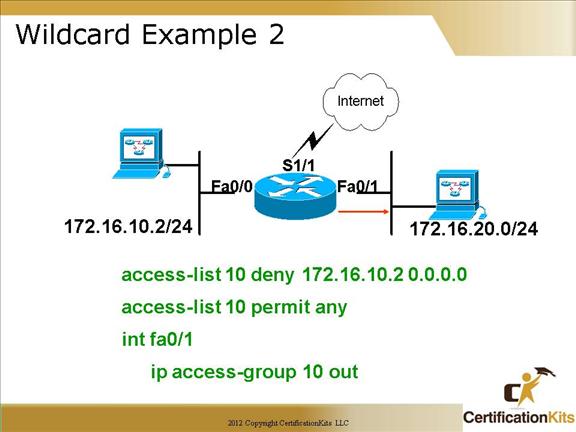
This example stops only host 172.16.10.2/32 from existing interface fa0/1. A host address is specified with a wildcard mask of 0.0.0.0 which if you remember from previous slides a 0 in a bit position means match exactly. Since a wildcard of 0.0.0.0 has a 0 in all 32 bit positions, all 32 bit must match exactly, hence it specifies a host address.
Cisco CCNA Wildcard Example 3
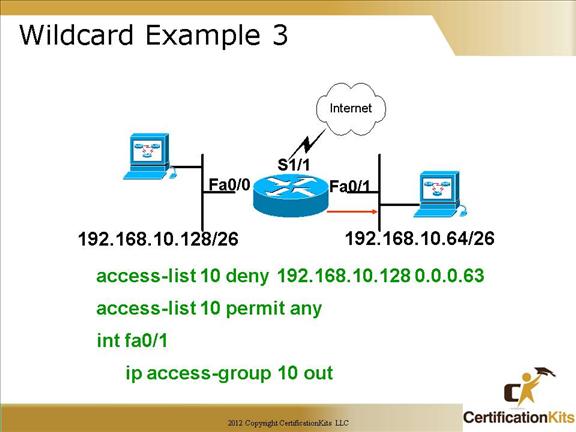
This example will deny anyone on subnet 192.168.10.128/26 (192.168.10.128 – 192.168.10.191) from exiting interface fa0/1. The wildcard mask specified in the example, 0.0.0.63 specifies the first three octets must match exactly while the last 6 bits in the fourth octet can be anything which means is can be in the range 128 – 191.
Cisco CCNA Wildcard Question
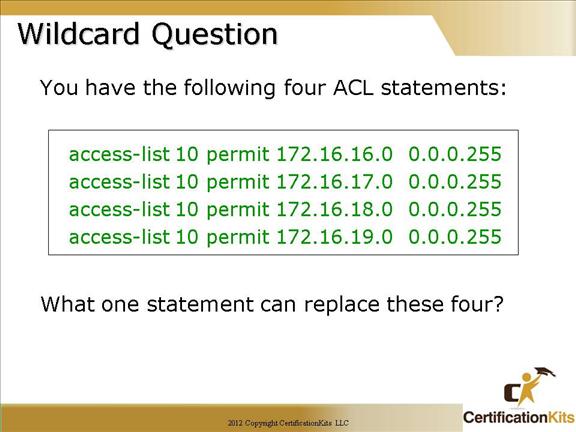
Answer:
access-list 10 permit 172.16.16.0 0.0.3.255
Since in the third octet, 16, 17, 18, and 19 can be summarized into one address it can be written as 172.16.16.0 0.0.3.255. Note, this can only be accomplished it the addresses are contiguous and start on subnet boundaries.
Cisco CCNA Applying Access lists to a VTY Line
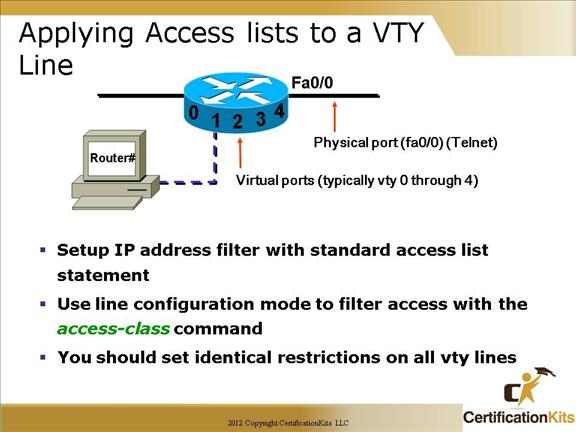
When you apply an access to the VTY lines, you don’t need to specify the telnet protocol since access to the VTY implies terminal access.
You also don’t need to specify a destination address, since it really doesn’t matter which interface address the user used as a target for the telnet session.
You really only need to control where the user is coming from—their source IP address. Hence, limiting vty access is accomplished utilizing standard IP access lists. They are applied to vty lines with an access-class command versus an ip access-group command utilized when applying ACLs to an interface.
An example follows on the next slide.
Cisco CCNA Virtual Terminal Access Example

The above example permits only hosts in network 192.89.55.0 to connect to the router’s VTY lines. Hence remote access is limited to only addresses in the range 192.89.55.0 – 192.89.55.255. The range is specified by the wildcard mask of 0.0.0.255.
