Cisco CCNA Standard versus Extended Access List
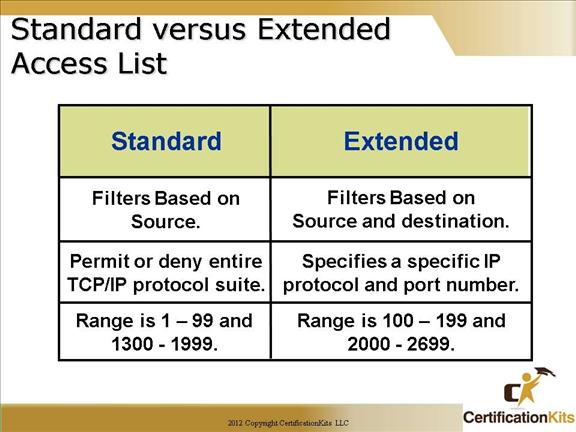
Standard access lists
These use only the source IP address in an IP packet as the condition test. All decisions are made based on source IP address. This means that standard access lists basically permit or deny an entire suite of protocols. They don’t distinguish between any of the many types of IP traffic such as WWW, telnet, UDP, etc.
Extended access lists
Extended access lists can evaluate many of the other fields in the layer 3 and layer 4 header of an IP packet.
IP Source Address
IP Destination Address
Protocol Field in Network Layer Packet
Port number in Transport Layer Segment
Cisco CCNA Extended Access List Example
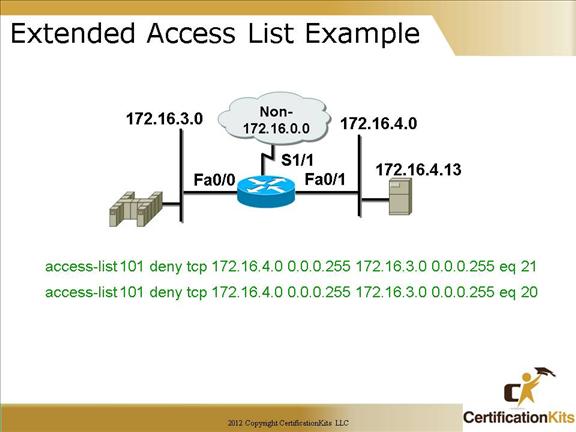
This slide shows an example of an extended IP access list.
It denies FTP (port 21 is FTP and port 20 is FTP data) from subnet 172.16.4.0 to 172.16.3.0. Actually since there is an implicit DENY at the end of each access list, this access list denies all packets since there is NOT a permit statement. Note: If access list 101 were applied to an interface, all traffic either inbound or outbound (depending on how the ACL was applied) would be denied.
As a general rule, all ACLs should have at least 1 permit rule.
Cisco CCNA Extended Access List Example
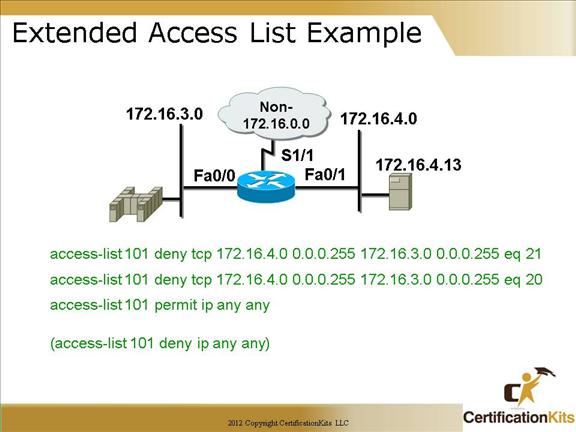
Taking the previous example a little further, it the intent of the ACL is to deny FTP from 172.16.4.0/24 to 172.16.3.0/24 but permit all other traffic then the following permit statement needs to be added after the deny statements:
access-list 101 permit ip any any
Access list 101 could be applied inbound to interface Fa0/1 or outbound to interface Fa0/0.
Remember there is an implicit deny ip any any at the end of every ACL.
Cisco CCNA Extended Access List Example
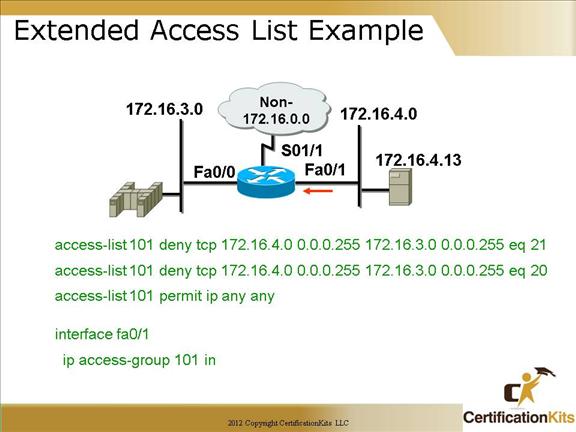
Now that the ACL has been defined, it needs to be applied to an interface. As stated on the previous slide, it can be applied with to fa0/1 in the inbound direction or fa0/0 in the outbound direction.
Following the general rule learned earlier in the course, extended ACLs should be placed close to the source while standard ACLs should be placed close to the destination. Since ACL 101 is an extended ACL it is applied closest to the source in the inbound direction utilizing the following commands:
interface fa0/1
ip access-group 101 in
Cisco CCNA Extended Access List Example
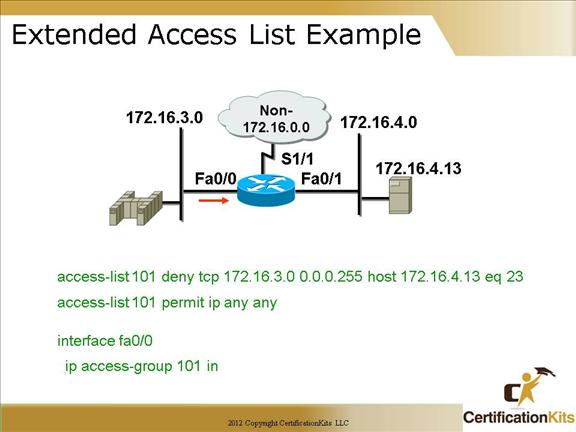
This slide demonstrates an extended access-list that will deny any source address from network 171.16.3.0 telnetting to host 172.16.4.13. Note: TCP port 23 equates to telnet. There is a permit ip any any at the end of the deny so all traffic other than the specified telnet is allowed. Again, since the ACL is an extended ACL it is applied as close to the source as possible.
Cisco CCNA Extended Access List Example
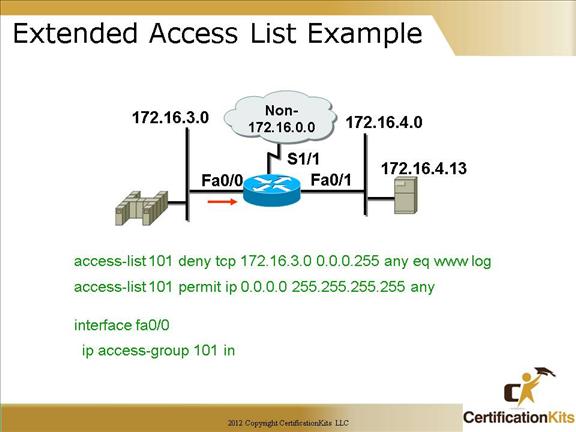
This slide demonstrates an extended access-list that will deny any host from network 172.16.3.0 from using HTTP to any destination.
This example demonstrates the use of pre-defined port numbers. In the example www equates to port 80 which is the default port utilized from a browser when performing http.
Cisco CCNA Extended Access List Example
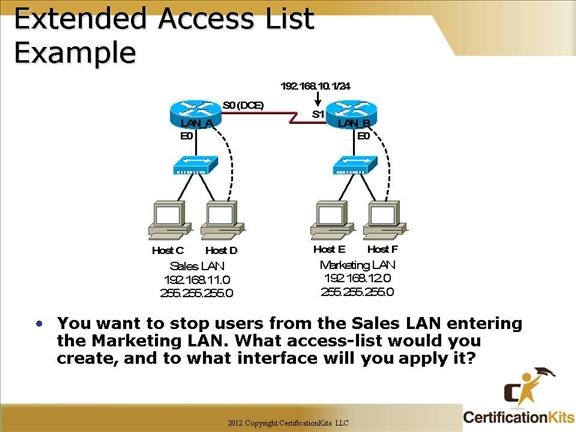
Extended:
On the LAN_A router
access-list 110 deny ip 192.168.11.0 0.0.0.255 192.168.12.0 0.0.0.255
access-list 110 permit ip any any
int e0
ip access-group 110 in
OR
Standard:
On the LAN_B router
access-list 10 deny 192.168.11.0 0.0.0.255
access-list 10 permit any
int e0
ip access-group 10 out
Cisco CCNA Access List Confihuration Guidelines

Guidelines
Access list numbers indicate which protocol is filtered.
One access list per interface, per protocol, per direction is allowed.
The order of access list statements controls testing.
Place the most restrictive statements at the top of list.
There is an implicit deny any statement as the last access list test. Every list needs at least one permit statement.
Create access lists before applying them to interfaces.
Access lists filter traffic going through the router; they do not apply to traffic originating from the router.
Cisco CCNA Named Access Lists

Named access lists are just another way to create standard and extended access lists. In medium to large enterprises, management of access lists can become, well, a real hassle over time.
For example, when you need to make a change to an access list, a frequent practice is to copy the access list to a text editor, change the number, edit the list, then paste the new list back into the router.
Named access lists allow you to use names to both create and apply either standard or extended access lists.
There is nothing new or different about these access lists aside from being able to refer to them in a way that makes sense to humans.
However, you do not need to delete the named access-list in order to make changes. This is one of the best benefits of named access-lists.
Cisco CCNA Named Standard ACL Example
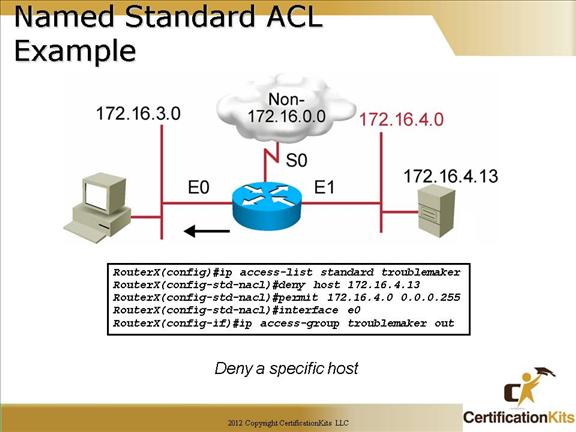
The “troublemaker” named standard ACL will deny host (172.16.4.13) from going out on E0 to subnet 172.16.3.0, all other hosts on subnet 172.16.4.0/24 will be allowed.
The arrow represent the access list is applied as an outbound access list on interface E0.
