Cisco CCNA Named Extended ACL Example
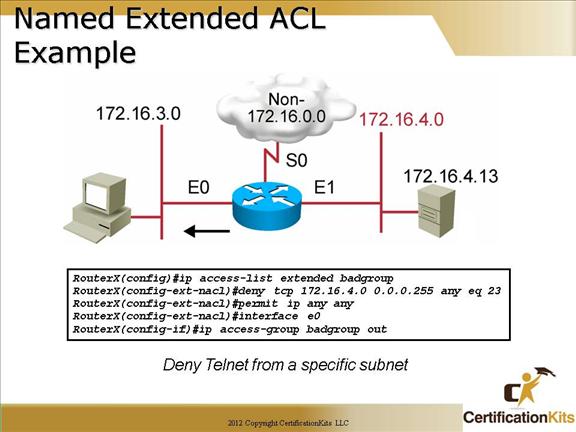
The “badgroup” named extended ACL will deny all telnet requests initiating on subnet 172.16.4.0 going out on E0 to subnet 172.16.3.0. All other traffic will be permitted. The ACL is applied in the outbound direction on interface E0.
Cisco CCNA Commenting ACL Satementss
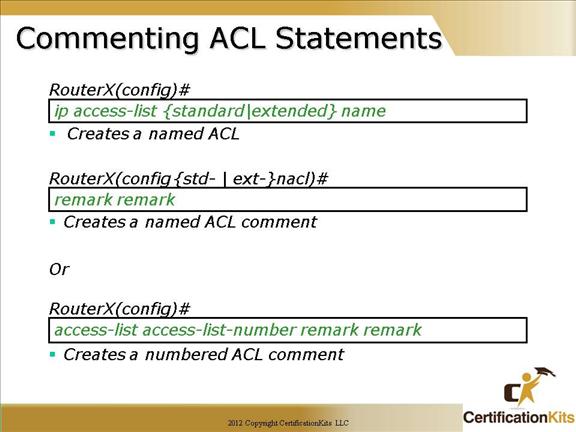
Comments can be placed within either named or numbered ACLs which helps with keeping track of what the ACL is supposed to do when someone other that the person who wrote the ACL looks at the configuration.
Comments are added to a named ACL from within named ACL configuration mode utilizing the remark remark command.
Comments are added to numbered ACLs by specifying the keyword “remark” rather than a permit or deny. The syntax is as follows:
access-list acl-number remark remark
Cisco CCNA Monitoring ACL Statements
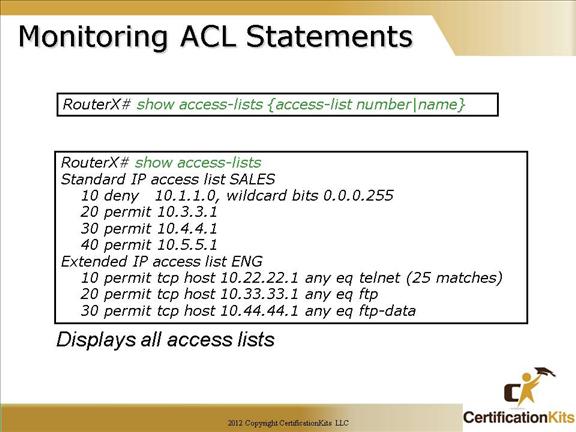
The “show access-list” command is the most consolidated method for seeing all access lists defined on the router at once.
The implicit deny all statement is not displayed unless it is explicitly entered in the access list. A good reason to add an explicit deny at the end of an ACL is to specify the log qualifier.
Cisco CCNA Verifying Access Lists

The “show ip int interface-name” command lists IP interface information. Indicates whether outgoing and/or inbound access lists are set.
Review the output of the “show ip interface” command displayed on the slide. The highlighted text shows details about access list settings in the show command output. The example output indicates there is not an outbound ACL set but there is an inbound ACL and the ACL number is 1.
Cisco CCNA Monitoring Access List Statements
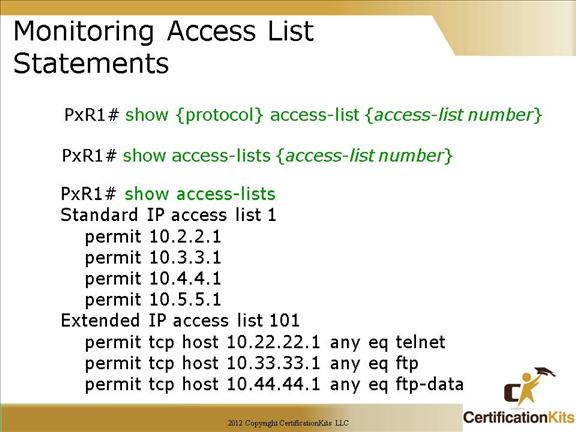
show access-list: Displays all access lists and their parameters configured on the router. This command does not show you which interface the list is applied to.
show access-list 110: Displays only the parameters for the access list 110. This command does not show you the interface the list is applied to.
show ip access-list: Displays only the IP access lists configured on the router.
show ip interface: Displays which interfaces have access lists set.
show running-config: Displays the access lists and which interfaces have access lists set.
Cisco CCNA Remember!

Two useful commands to quickly view information about ACLs and what interfaces they are applied to are:
show access-list
show ip interface
Cisco CCNA Match the Following:

Answer:
permit tcp any 192.168.47.4 0.0.0.0 eq 80 – Allow all web access to server 192.168.47.4
deny ip any 192.168.47.32 0.0.0.15 — Block all IP access to subnet 192.168.47.32/28
deny icmp any 192.168.47.5 0.0.0.31 — Block all ping messages only to server 192.168.47.5/27
permit ip 192.168.45.32 0.0.0.31 192.168.47.32 0.0.0.15 — Allow access from subnet 192.168.45.3/27 to subnet 192.168.47.3/28
Cisco CCNA Access List Question
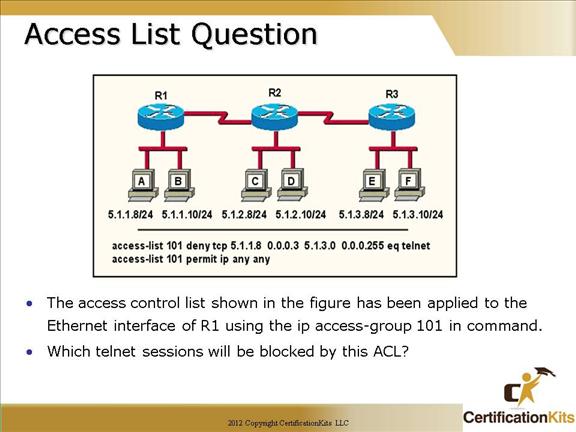
The following telnet session will be blocked by the ACL:
Any host with an address between 5.1.1.8 and 5.1.1.11 on R1 will not be able to telnet to network 5.1.3.0
Cisco CCNA Chapter 7 Summary

Cisco CCNA Chapter 7 Summary

