Cisco CCNA Security

In today’s world more so than ever before, securing your network from threats is extremely important. Network hackers are ever present and continually try to break into networks. Tools are so sophisticated these days that a person with little computer or network knowledge can easily attempt to break into networks.
The proper use and configuration of access lists is a vital part of router configuration because access lists are such versatile networking accessories. Contributing mightily to the efficiency and operation of your network, access lists give network managers a huge amount of control over traffic flow throughout the enterprise. With access lists, managers can gather basic statistics on packet flow and security policies can be implemented. Sensitive devices can also be protected from unauthorized access.
Cisco CCNA Common Threats to Physical Installations

Hardware threats: The threat of physical damage to the router or switch hardware. Mission-critical network equipment should be located in locked room with restricted access to only authorized personnel.
Environmental threats: Threats such as temperature extremes (too hot or too cold) or humidity extremes (too wet or too dry). The room should have dependable temperature and humidity control systems. If possible, remotely monitor and alarm the environmental parameters of the room.
Electrical threats – Threats such as voltage spikes, unconditioned power (noise), insufficient voltage (brownouts) and total power loss. Network equipment should be utilize redundant power supplies, be placed on uninterruptible power supply (UPS) for mission critical systems and monitored.
Maintenance threats: Maintenance threats include poor handling of equipment (ESD), lack of spares, poor cabling. Clearly label all equipment cabling and secure the cabling to equipment racks to prevent accidental damage, disconnection, or incorrect termination. Do not leave a console connected to and logged into any console port. Always log off administrative interfaces when leaving a station.
Cisco CCNA Network Security – Closed Networks
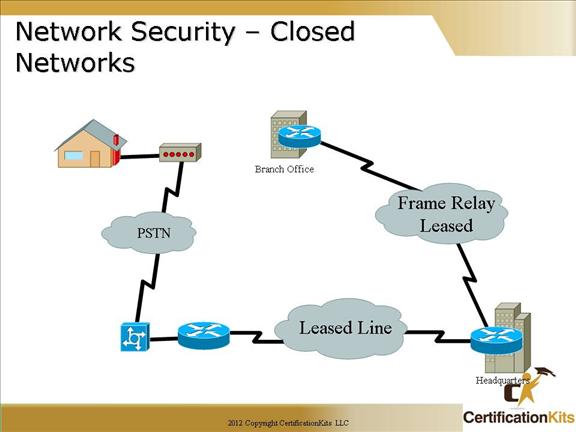
Closed Network – No outside connectivity (leased lines / dedicated circuits), networks designed in this way can be considered safe from outside attacks. It provides connectivity to only known trusted parties and sites. While it is considered safe from outside attacks, internal threats still exist.
Cisco CCNA- Open Networks
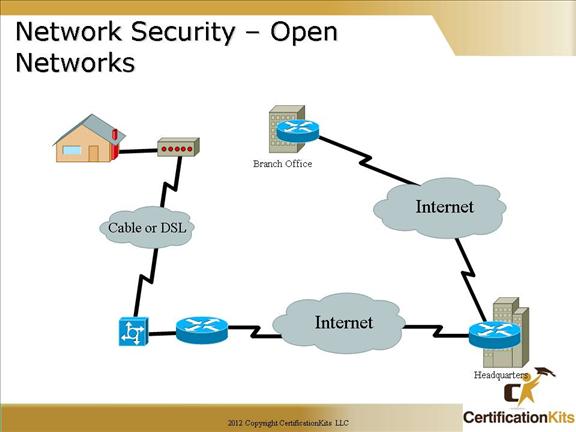
Open Network – Corporate networks require access to the Internet and other public networks. It is not uncommon for corporate networks have several access points to public and other private networks. Securing open networks is extremely important. Open networks have not only internal threats but external threats as well.
Cisco CCNA Balancing Network Security

It is difficult to find a balance between securing the network while still allowing valid traffic required to support business.
Security has moved to the forefront of network management and implementation. Most businesses survival depends on allowing open access to network resources and to ensure data and resources are as secure as possible. This is a very daunting task.
Cisco CCNA
There are numerous different classes of attacks. Some of which may include passive monitoring of communications, exploits by insiders with access to the system, distributed attacks from remote sites, close-in attacks and active network attacks.
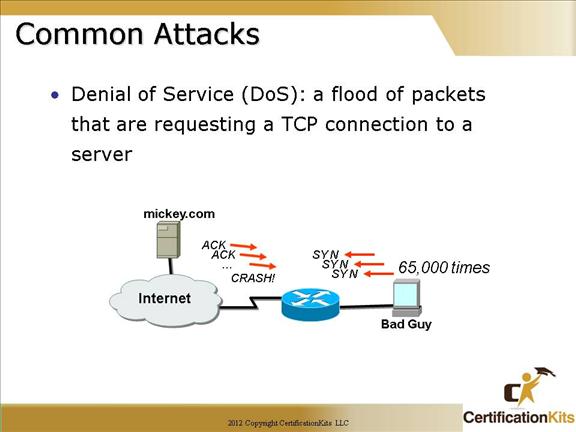
One common attack is a Denial of Service (DoS) attack. This is an attempt to make a computer resource unavailable to its intended users.
One common method of this attack involves saturating the target (victim) machine with external communications requests. In doing so, it cannot respond to legitimate traffic, or responds so slowly as to be rendered effectively unavailable. Generally speaking, DoS attacks are implemented by either forcing the targeted computer(s) to reset, or consuming its resources so that it can no longer provide its intended service or obstructing the communication media between the intended users and the victim so that they can no longer communicate adequately.
Cisco CCNA Security Appliances
Above are definitions of Intrusion Detection System (IDS) and Intrusion Prevention System (IPS).
Cisco CCNA Securing unused Switch Ports
Good security practice is to disable unused switch ports utilizing the “shutdown” command from within interface configuration mode. It is also good security practice to place the unused port in an unused VLAN utilizing the “switchport mode access” and “switchport access vlan #” commands.
Cisco CCNA Port Security
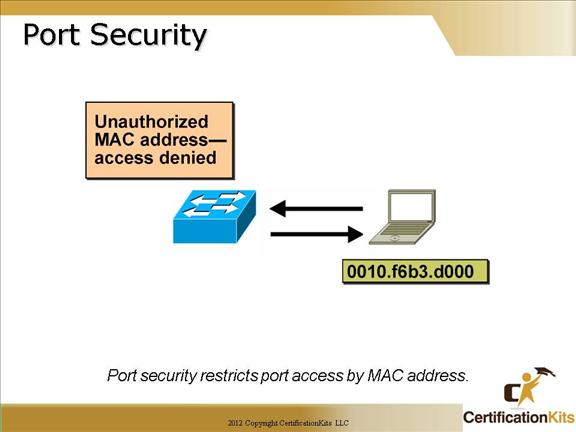
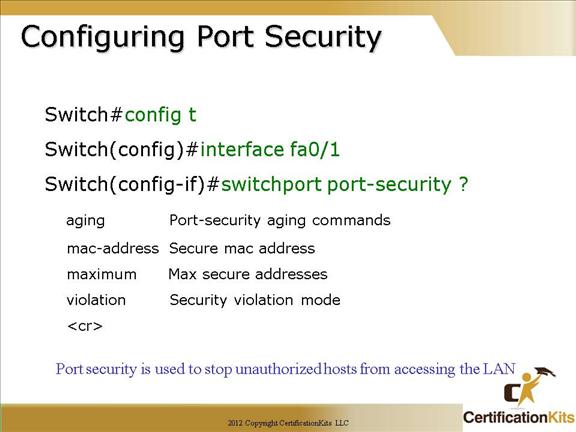
To enable port security on an interface utilize the to switchport port-security interface command with appropriate parameters.
Options are as follows:
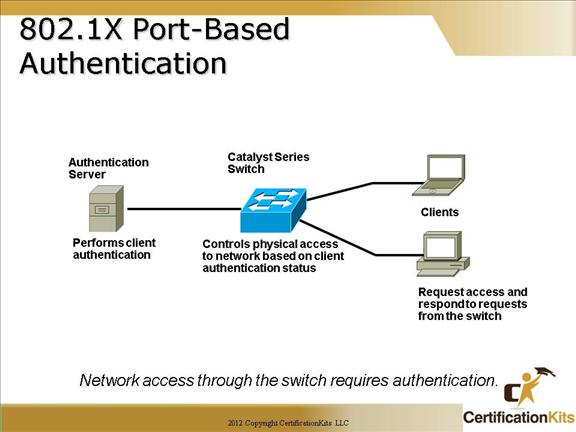
switchport port-security {mac-address mac-address | mac-address sticky maximum value | violation {restrict | shutdown}] Note: Available options vary between different switch types and different IOS versions. Cisco CCNA Configuring Port Security If you are using sticky addresses, then this sets up time limits Switch(config-if)# switchport port-security aging ? static Enable aging for configured secure addresses time Port-security aging time type Port-security aging type Sticky means you don’t care what the addresses are. Switch(config-if)# switchport port-security mac-address ? H.H.H 48 bit mac address sticky Configure dynamic secure addresses as sticky Sets the maximum amount of MAC addreses that can be associated with a port Switch(config-if)# switchport port-security maximum ? Maximum addresses Switch(config-if)# switchport port-security violation ? protect Security violation protect mode (logs it) restrict Security violation restrict mode (suspends it) shutdown Security violation shutdown mode Once you have defined it….Don’t forget to turn it on! Cisco CCNA Port Security Examples The port security feature on a Cisco switch can be used to restrict input to an interface by identifying and limiting specific MAC addresses allowed to access the port. When secure MAC addresses are assigned to a secure port, the port does not forward packets with source addresses outside the group of defined addresses. The command switchport port-security max 1 sets the maximum number of MAC addresses learned off the port to 1. When used in combination with the switchport port-security violation shutdown command, the port will be placed in err-disable mode if a violation occurs. Cisco CCNA 802.1X Port-Based Authentication •Client—the device (workstation) that requests access to the LAN and switch services and responds to requests from the switch. The workstation must be running IEEE 802.1x-compliant client software such as that offered in the Microsoft Windows operating systems. (The client is the supplicant in the IEEE 802.1x specification.) •Authentication server—performs the actual authentication of the client. The authentication server validates the identity of the client and notifies the switch whether or not the client is authorized to access the LAN and switch services. Because the switch acts as the proxy, the authentication service is transparent to the client. In this release, the RADIUS security system with Extensible Authentication Protocol (EAP) extensions is the only supported authentication server. It is available in Cisco Secure Access Control Server Version 3.0 or later. RADIUS operates in a client/server model in which secure authentication information is exchanged between the RADIUS server and one or more RADIUS clients. •Switch (edge switch or wireless access point)—controls the physical access to the network based on the authentication status of the client. The switch acts as an intermediary (proxy) between the client and the authentication server, requesting identity information from the client, verifying that information with the authentication server, and relaying a response to the client. The switch includes the RADIUS client, which is responsible for encapsulating and decapsulating the EAP frames and interacting with the authentication server.