Cisco CCNA Wireless Troubleshooting

Troubleshooting wireless by breaking the environment into wired network versus wireless network. Then further divide the wireless network into configuration versus RF issues. First verify the proper operation of the existing wired infrastructure and associated services. Verify other pre-existing Ethernet attached host can renew their DHCP address and reach the Internet. Then co-located both the access point and wireless client together to verify configuration and remove issues of possible RF since they are both co-located. Always start the wireless client on open authentication and establish connectivity. Then progress with desired for of wireless security. If wireless client is operational at this point of co-location, then only RF related issue remain. First consider if metal obstructions exist. If so, then move the obstruction or location of access point. If the distance is too great, consider adding another access point using same SSID but unique RF channel. Lastly but more common to consider is RF environment.
Just like a wired network can become congested with traffic, so can RF for 2.4 GHz more often than 5 GHz. Are there other sources of wireless devices using 2.4 GHz. Note if performance issue seem to relate to time of day which would indicate the usage pattern of suspect RF interference device. Easy example would be slow performance that relates to noon time in the office near the break room where there is a microwave oven used for employees to heat up lunch. While most microwave will practically RF jam channel 11, other microwave based on manufacture will jam all RF channels. More difficult might be RF devices that hop frequencies like FHSS used in cordless phones. Since there can be many sources of RF interference, always start with co-locating the access point and wireless client and then move the wireless client until reproducing the problem. Most often, wireless clients will have supplicant software to assist in the effort by presenting relative RF signal strength and qualify.
Cisco CCNA Wireless LAN Security Threats
With the lower costs of IEEE 802.11b/g systems, it is inevitable that hackers will have many more unsecured WLANs from which to choose.
Incidents have been reported of people using numerous open source applications to collect and exploit vulnerabilities in the IEEE 802.11 standard security mechanism, Wired Equivalent Privacy (WEP).
Wireless sniffers enable network engineers to passively capture data packets so that they can be examined to correct system problems. These same sniffers can be used by hackers to exploit known security weaknesses.
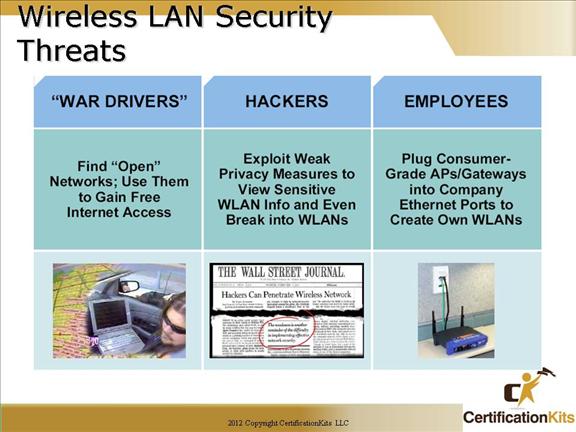
“War driving” is a phrase that was originally used to describe someone who is using a cellular scanning device looking for cell phone numbers to exploit. War driving also refers to someone driving around with a laptop and an 802.11b/g client card looking for an 802.11b/g system to exploit.
Most wireless devices sold today are wireless network ready. End users often do not change default settings or they implement only standard WEP security, which is not optimal solution for secure wireless networks.
With basic WEP encryption enabled (or, obviously, with no encryption enabled), it is possible to collect data and obtain sensitive network information, such as user login information, account numbers, and personal records.
A rogue AP is an AP that has been placed on a WLAN and that might be used to interfere with normal network operations (DoS attacks, for example). If this rogue AP is programmed with the correct WEP key, client data may be captured. This AP may also be configured to provide unauthorized users with information about the network, such as MAC addresses of clients (both wireless and wired), the ability to capture and spoof data packets, and at worst, access to servers and files. A simple and common version of rogue AP are those employees unknowning install. Employees install access points intended for home use without the necessary security configuration on the enterprize network causing a security risk for the network.
Cisco CCNA Mitigating the Threats
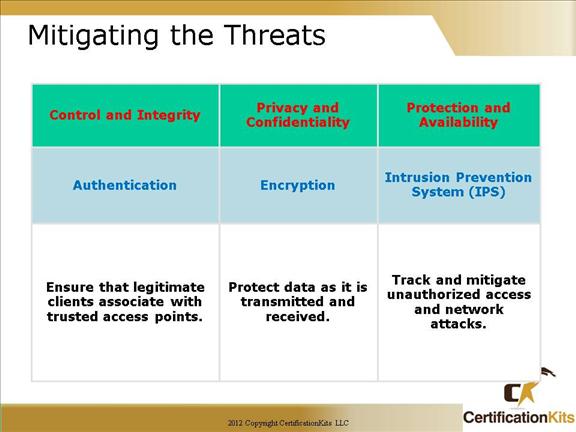
To secure a WLAN, the following steps are required:
– Authentication to ensure that legitimate clients and users access the network via trusted access points
– Encryption for providing privacy and confidentiality
– Protection from security risks and availability with intrusion detection and intrusion protection systems for WLANs
The fundamental solution for wireless security is authentication and encryption to protect the wireless data transmission. These two wireless security solution can be implemented in a various degrees, however both apply to SOHO and large enterprise wireless networks. Larger enterprise networks will need additional levels of security offered by Intrusion Detection Systems (IDS) monitor. Current IDS systems can not only detect wireless network attacks, but also provide basic mitigation against foreign clients and access points. Many enterprise networks use IDS not just for protection against outside threats, but mainly for unintentional unsecured access points installed by employees desiring the mobility and benefits of wireless.
Cisco CCNA Evolution of Wireless LAN Security
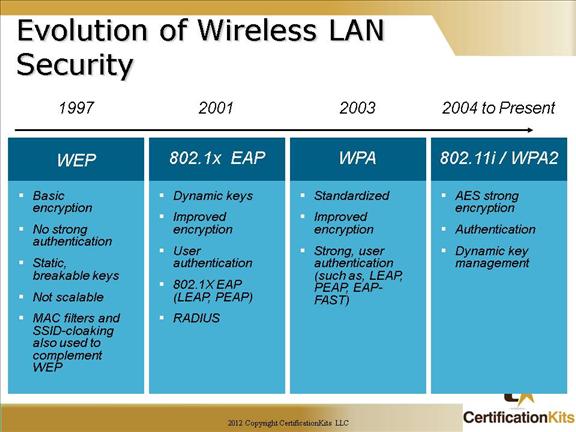
The figure shows the evolution of wireless LAN (WLAN) security.
Initially, IEEE 802.11 security only defined 64-bit static WEP keys for both encryption and if used authentication. The 64-bit key contained the actual 40-bit key plus 24-bit Initialization Vector (IV). The authentication method was not strong and the keys were eventually compromised. Because the keys were administered statically, this method of security was not scalable to large enterprise environments. Enterprise companies tried to supplement this weakness with techniques using SSID and MAC address filtering.
The SSID is a network-naming scheme and configurable parameter that both the client and the AP must share. If the client does not have the proper SSID advertised from the access point configured to not broadcast the SSID (SSID Cloaking), it is unable to associate with the AP and would have no access to the network. The problem with the effort was that 802.11 allows wireless client to use a null string (no value entered into the SSID field) thereby requesting that the AP to broadcast its SSID rendering the security effort ineffective. Access point also supported filtering using a MAC address. Tables are manually constructed on the AP to allow or disallow clients based upon their physical hardware address. However MAC addresses may be relatively easily spoofed and MAC address filtering is not considered a security feature either.
While 802.11 committee then began the process of upgrading the security of the WLAN, Enterprise customers needed wireless security immediately to enable deployment. Driven by customer demand, Cisco introduced early proprietary enhancements to RC4-based WEP encryption. Cisco implemented Cisco’s Temporal Key Integrity Protocol (CKIP) per-packet keying or hashing and Cisco’s Message Integrity Check (CMIC) to protect WEP keys. Cisco also adapted the use of IEEE 802.1X wired authentication protocols on wireless and dynamic keys using Lightweight EAP (LEAP) to a centralized database.
Soon after Cisco wireless security implementation, the Wi-Fi Alliance introduced Wi-Fi Protected Access (WPA) as an interim solution that was a subset of the expected 802.11i security standard for WLANs using 802.1X authentication and improvements to WEP encryption. The newer key hashing (TKIP versus CKIP) and message integrity check (MIC versus CMIC) where similar in feature but not compatible.
Today IEEE 802.11i has been ratified and Advanced Encryption Standard (AES) has replaced Wired Equivalent Privacy (WEP) as the latest and most secure method of encrypting data. Wireless intrusion detection systems are available to identify and protect the WLAN from attacks. The Wi-Fi Alliance certifies 802.11i devices under Wi-Fi Protected Access 2 (WPA2).
Cisco CCNA Wireless Client Association
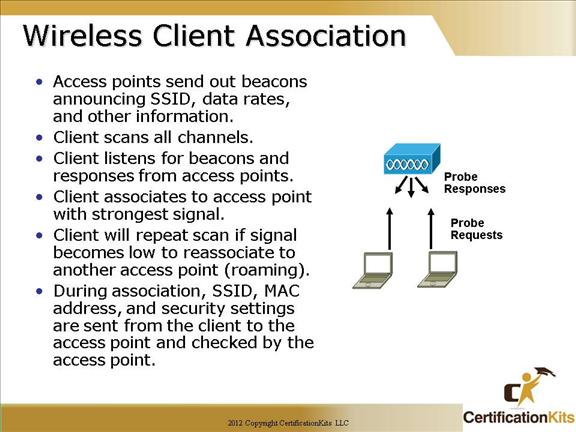
Access points send out beacons announcing one or more SSIDs, data rates, and other information. The client scans all the channels and listens for beacons and responses from the access points. The client associates to the access point that has the strongest signal. If the signal becomes low, the client repeats the scan to associate with another access point (roaming). During association, the SSID, MAC address, and security settings are sent from the client to the access point and checked by the access point
Wireless client’s association to a selected access point is actually the 2nd of a two step process. Both authentication and association must occur in that order before an 802.11 client can pass traffic through the access point to another host on the network. Client authentication at this initial process is not the same as network authentication, entering username and password to get access to the network. Authentication is simply the first step (followed by association) between the wireless client and access point only to establish communication. The 802.11 standard only specified two different methods of authentication Open Authentication or Shared Key Authentication. Open authentication is simply the exchange of four hello type packets with no client or access point verification to allow ease of connectivity. Shared Key authentication uses a static defined WEP key know between the client and access point for verification. This same key may or may not be used to encrypt the actual data passing between wireless client and access point based on user configuration.
Cisco CCNA How 802.1X Works on the WLAN
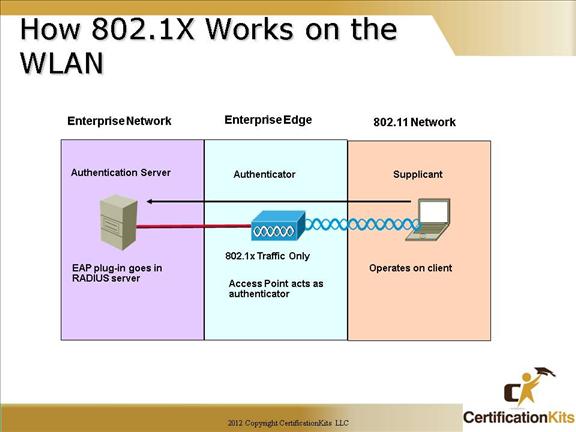
The access point, acting as the authenticator at the enterprise edge, allows the client to associate using open authentication. The access point then encapsulates any 802.1X traffic bound for the authentication server and sends it to the server. All other network traffic is blocked, meaning that all other attempts to access network resources are blocked.
Upon receiving RADIUS traffic bound for the client, the access point encapsulates it and sends the information to the client. Although the server authenticates the client as a valid network user, this process allows the client to validate the server as well, ensuring that the client is not logging into a phony server.
While an enterprise network will use a centralized authentication server, smaller offices or business might simply use the access point with preshared keys as the authentication server for wireless clients.
Cisco CCNA WPA and WPA2 Modes
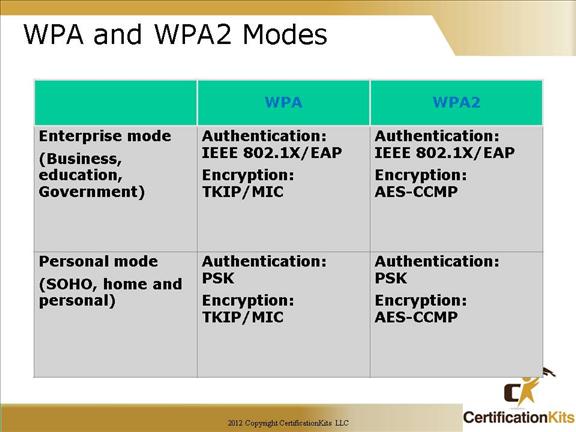
WPA provides authentication support via IEEE 802.1X and Preshared Key (PSK) (IEEE 802.1X recommended for enterprise deployments). WPA provides encryption support via TKIP. TKIP includes message identity check (MIC) and per-packet keying (PPK) via initialization vector (IV) hashing and broadcast key rotation.
In comparison to WPA, WPA2 authentication is not changed but encryption used is AES-CCMP.
Enterprise Mode
Enterprise Mode is a term given to products that are tested to be interoperable in both PSK and IEEE 802.1x/EAP modes of operation for authentication. When IEEE 802.1x is used, an authentication, authorization, and accounting (AAA) server (the RADIUS protocol for authentication and key management and centralized management of user credentials) is required. Enterprise Mode is targeted to enterprise environments.
Personal Mode
Personal Mode is a term given to products tested to be interoperable in the PSK-only mode of operation for authentication. It requires manual configuration of a pre-shared key on the AP and clients. PSK authenticates users via a password, or identifying code, on both the client station and the AP. No authentication server is needed. Personal Mode is targeted to SOHO environments.
