Cisco CCNP SWITCH Dynamic Host Configuration Protocol
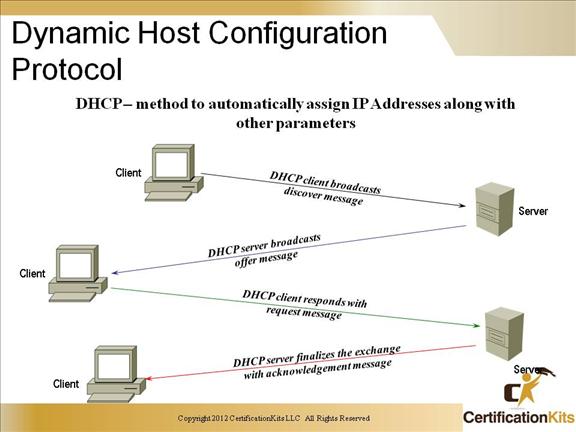
DHCP is used to assign IP addresses automatically and to set TCP/IP stack configuration parameters, such as the subnet mask, default router, and Domain Name System (DNS) servers. DHCP is also used to provide other configuration information as necessary, including the length of time the address has been allocated to the host. DHCP consists of two components: a protocol for delivering host-specific configuration parameters from a DHCP server to a host, and a mechanism for allocating network addresses to hosts.
Using DHCP, a host can obtain an IP address quickly and dynamically. All that is required is a defined range of IP addresses on a DHCP server. As hosts come online, they contact the DHCP server and request address information. The DHCP server selects an address and allocates it to that host. The address is only leased to the host, so the host will periodically contact the DHCP server to extend the lease. This lease mechanism ensures that hosts that have been moved or are switched off for extended periods of time do not hold on to addresses that they do not use. The addresses are returned to the address pool by the DHCP server, to be reallocated as necessary.
Cisco CCNP SWITCH DHCP Snooping
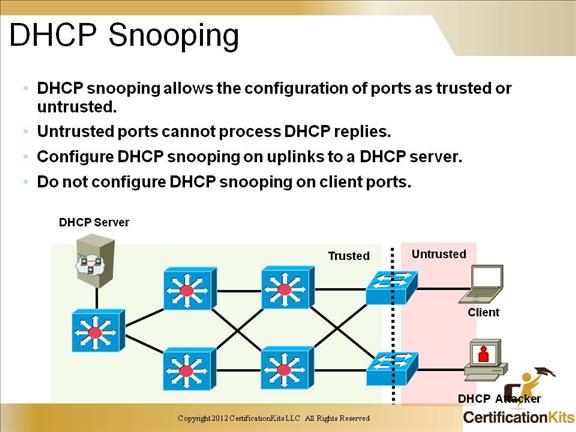
DHCP snooping is a Cisco Catalyst feature that determines which switch ports can respond to DHCP requests. Ports are identified as trusted and untrusted. Trusted ports can source all DHCP messages, whereas untrusted ports can source requests only. Trusted ports host a DHCP server or can be an uplink toward the DHCP server.
- Enable DHCP snooping globally.
Switch(config)# ip dhcp snooping
By default, the feature is not enabled.
2. Enable DHCP Option 82.
Switch(config)# ip dhcp snooping information option
This is optional for the forwarded DHCP request packet to contain information on the switch port where it originated.
3. Configure DHCP server interfaces or uplink ports as trusted.
Switch(config-if)# ip dhcp snooping trust
At least one trusted port must be configured. Use the no keyword to revert to untrusted.By default, all ports are untrusted.
4. Configure the number of DHCP packets per second (pps) that are acceptable on the port.
Switch(config-if)# ip dhcp snooping limit rate
rateConfigure the number of DHCP pps that an interface can receive. Normally, the rate limit applies to untrusted interfaces. This is used to prevent DHCP starvation attacks by limiting the rate of the DHCP requests on untrusted ports.
Cisco CCNP SWITCH Dynamic ARP Inspection
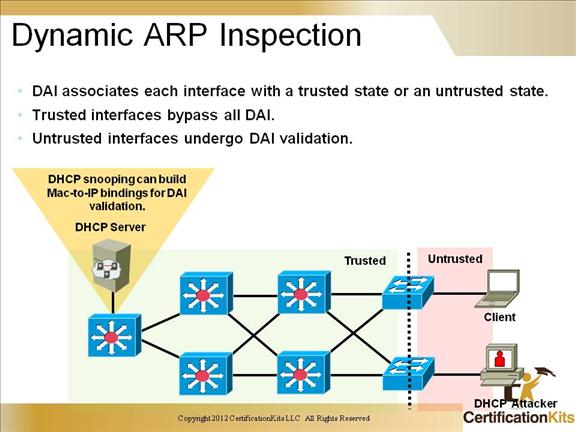
Dynamic ARP Inspection (DAI) determines the validity of an ARP packet based on a valid MAC-address-to-IP-address bindings database built by DHCP snooping. In addition, to handle hosts that use statically configured IP addresses, DAI can also validate ARP packets against user-configured ARP ACLs.
To ensure that only valid ARP requests and responses are relayed, DAI takes these actions:
– Forwards ARP packets received on a trusted interface without any checks
– Intercepts all ARP packets on untrusted ports
– Verifies that each intercepted packet has a valid IP-to-MAC address binding before forwarding packets that can update the local ARP cache
– Drops, logs, or drops and logs ARP packets with invalid IP-to-MAC address bindings
Cisco CCNP SWITCH Cisco Discovery Protocol
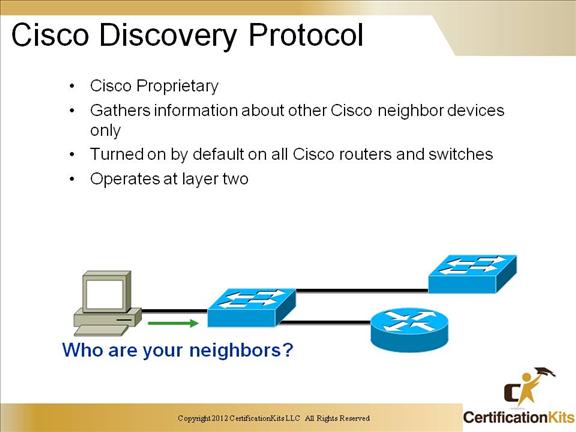
Cisco Discovery Protocol (CDP) is a proprietary protocol designed by Cisco to help administrators collect information about both locally attached and remote devices.
By using CDP, you can gather hardware and protocol information about neighbor devices, regardless of the routed protocols enabled on the interface since it operates at layer 2. This is very useful information for troubleshooting and documenting your Cisco-based networks. CDP is turned on by default on all Cisco routers and switches.
Cisco CCNP SWITCH Cisco Discovery Protocol
The show cdp neighbor command (sh cdp nei for short) delivers information about directly connected devices.
It’s important to remember that CDP packets aren’t passed through a Cisco switch, and that you only see what’s directly attached. So this means that if your a router is connected to a switch, you won’t see any of the devices hooked up to that switch, you will need to get that information from the switch itself.
Another valuable CDP command to get more information about a neighbor is the show cdp neighbor detail command (show cdp nei de for short). This command can be run on both routers and switches, and it displays detailed information about each device connected to the device you’re running the command on.
The “show cdp entry *” command is the same as show cdp nei detail. However, on a router or switch, type show cdp entry * ? and you’ll see there are two helpful subcommands you can use.
Cisco CCNP SWITCH show cdp neighbors
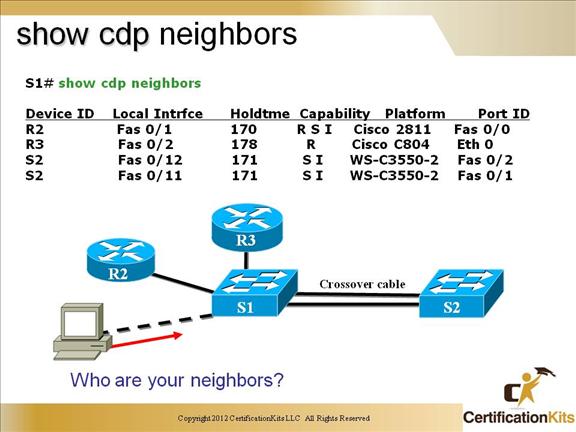
Field Descriptions:
Device ID – The configured ID (name), MAC address, or serial number of the neighbor device.
Local Intrfce – (Local Interface) The protocol being used by the connectivity media.
Holdtime – (Holdtime) The remaining amount of time, in seconds, the current device will hold the CDP advertisement from a transmitting router before discarding it.
Capability – The capability code discovered on the device. This is the type of the device listed in the CDP Neighbors table.
Platform – The product number of the device.
Port ID – The protocol and port number of the device.
Command syntax:
show cdp neighbors
type – (Optional) Type of the interface connected to the neighbors about which you want information.
number – (Optional) Number of the interface connected to the neighbors about which you want information.
detail – (Optional) Displays detailed information about a neighbor (or neighbors) including network address, enabled protocols, hold time, and software version.
