Cisco CCNP SWITCH Private VLANS
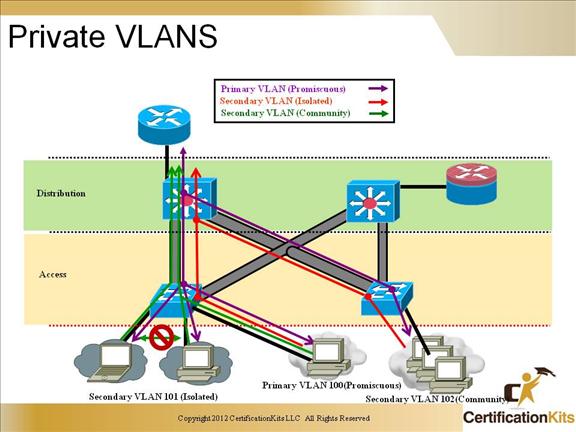
Service providers often have devices from multiple clients, in addition to their own servers, on a single Demilitarized Zone (DMZ) segment or VLAN. As security issues proliferate, it becomes necessary to provide traffic isolation between devices, even though they may exist on the same Layer 3 segment and VLAN. Catalyst 6500/4500/3750 switches implement PVLANs to keep some switch ports shared and some switch ports isolated, although all ports exist on the same VLAN. The 2950/2960 and 3550/3560 support “protected ports,” which are functionality similar to PVLANs on a per-switch basis.
Cisco CCNP SWITCH PVLAN Port Types

Isolated: An isolated port has complete Layer 2 separation from other ports within the same PVLAN, except for the promiscuous port. PVLANs block all traffic to isolated ports, except the traffic from promiscuous ports. Traffic received from an isolated port is forwarded to only promiscuous ports.
Promiscuous: A promiscuous port can communicate with all ports within the PVLAN, including the community and isolated ports. The default gateway for the segment would likely be hosted on a promiscuous port, given that all devices in the PVLAN will need to communicate with that port.
Community: Community ports communicate among themselves and with their promiscuous ports. These interfaces are isolated at Layer 2 from all other interfaces in other communities, or in isolated ports within their PVLAN.
PVLAN ports are associated with a set of supporting VLANs that are used to create the PVLAN structure. A PVLAN uses VLANs in three ways:
As a primary VLAN: Carries traffic from promiscuous ports to isolated, community, and other promiscuous ports in the same primary VLAN.
As an isolated VLAN: Carries traffic from isolated ports to a promiscuous port.
As a community VLAN: Carries traffic between community ports and to promiscuous ports. You can configure multiple community VLANs in a PVLAN.
Isolated and community VLANs are called secondary VLANs. You can extend PVLANs across multiple devices by trunking the primary, isolated, and community VLANs to other devices that support PVLANs.
Cisco CCNP SWITCH Configuring PVLANs
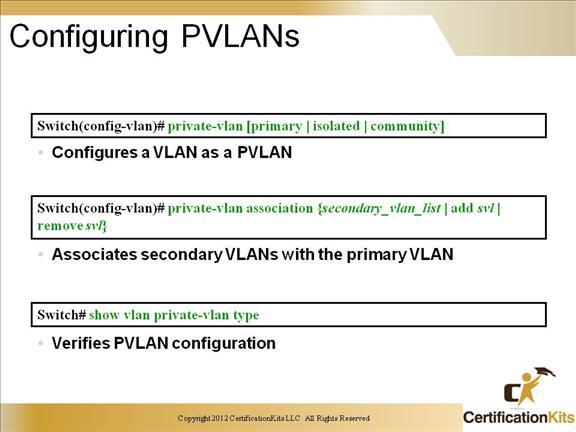
Basic steps to congfigure PVLANs.
– Set VTP mode to transparent.
– Create the secondary VLANs.
– Isolated and community VLANs are secondary VLANs.
– Create the primary VLAN.
– Associate the secondary VLAN with the primary VLAN. Only one isolated VLAN can be mapped to a primary VLAN, but more than one community VLAN can be mapped to a primary VLAN.
– Configure an interface as an isolated or community port.
– Associate the isolated port or community port with the primary-secondary VLAN pair.
– Configure an interface as a promiscuous port.
-Map the promiscuous port to the primary-secondary VLAN pair.
– Use these commands to configure a VLAN as a PVLAN:
Switch(config)#vlan vlan_ID
Switch(config-vlan)#
Cisco CCNP SWITCH Configuring PVLAN Ports
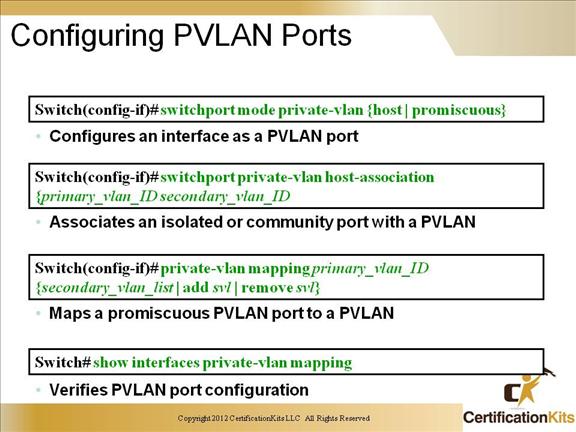
Here are best practices to consider when you configure a Layer 2 interface as a PVLAN promiscuous port:
– The secondary_vlan_list parameter cannot contain spaces. It can contain multiple comma-separated items. Each item can be a single PVLAN ID or a hyphenated range of PVLAN IDs.
– Enter a secondary_vlan_list or use the add keyword with a secondary_vlan_list to map the secondary VLANs to the PVLAN promiscuous port.
– Use the remove keyword with a secondary_vlan_list to clear the mapping between secondary VLANs and the PVLAN promiscuous port.
– Use the no keyword to clear all mapping from the PVLAN promiscuous port.
Cisco CCNP SWITCH EtherChannel Guidelines
EtherChannels offer the following benefits:
- • Logical aggregation of similar links
- • Viewed as one logical port
- • Switch-level load balancing
- • Redundancy
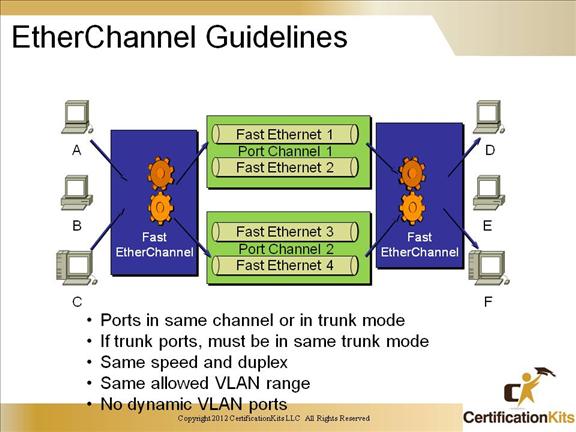
In order to successfully deploy EtherChannel you must follow some simple rules:
- • Ports in same channel or in trunk mode
- • If trunk ports, must be in same trunk mode
- • Same speed and duplex
- • Same allowed VLAN range
- • No dynamic VLAN ports
Cisco CCNP SWITCH EtherChannel Guidelines
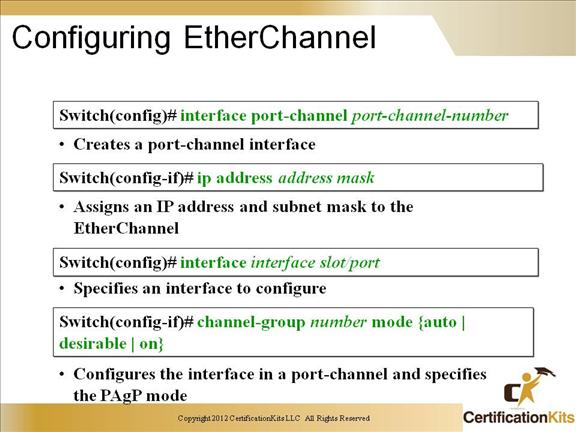
Slide displays the minimal commands necessary to configure EtherChannel (creation of a port channel interface).
Cisco CCNP SWITCH Verifying EtherChannel
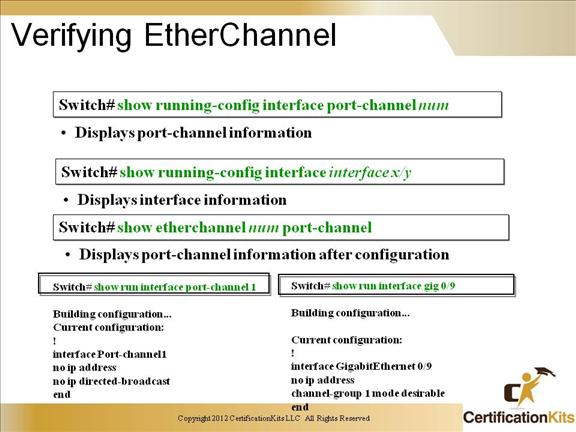
interface Port-channel2
switchport trunk encapsulation dot1q
switchport mode trunk
switchport nonegotiate
no ip address
!
interface GigabitEthernet0/9
description DSW121 0/9-10 — DSW122 0/9-10
switchport trunk encapsulation dot1q
switchport mode trunk
switchport nonegotiate
no ip address
duplex full
speed 100
channel-group 2 mode desirable
!
interface GigabitEthernet0/10
description DSW121 0/9-10 — DSW122 0/9-10
switchport trunk encapsulation dot1q
switchport mode trunk
switchport nonegotiate
no ip address
duplex full
speed 100
channel-group 2 mode desirable
!
Cisco CCNP SWITCH Configuring PAgP and LACP
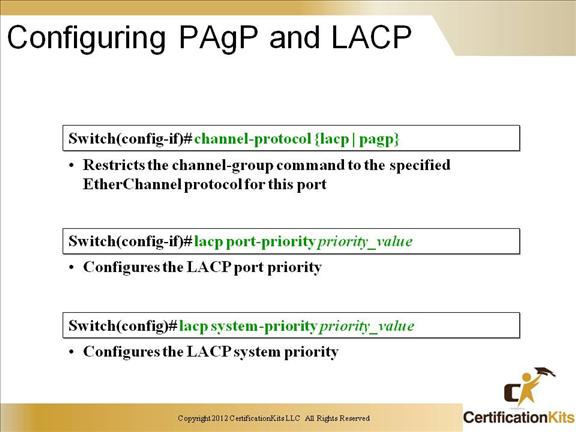
Port Aggregation Protocol (PAgP) is a Cisco-proprietary protocol that is used to expedite the automatic creation of EtherChannels by exchanging packets between Ethernet interfaces.
Link Aggregation Control Protocol (LACP) is defined in IEEE 802.3ad. It configures the maximum number of compatible ports in a channel, up to the maximum allowed by the hardware (eight ports).
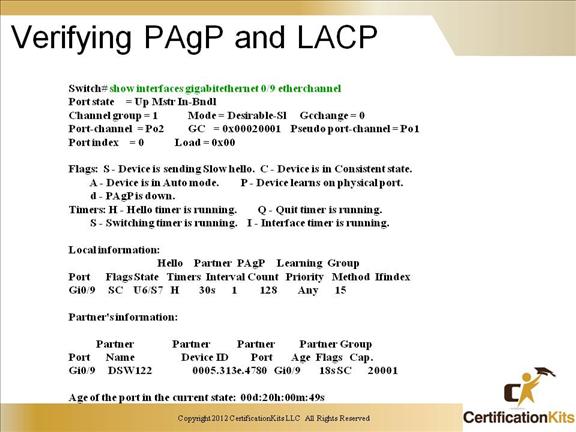
Cisco CCNP SWITCH Verifying PAgP and LACP