Cisco CCNP SWITCH Minimizing Service Loss and Data Theft in a Campus Network

Cisco CCNP SWITCH Switch Attack Categories

Layer 2 malicious attacks are typically launched by a device that is connected to the campus network. This can be a physical rogue device placed on the network for malicious purposes or an external intrusion that takes control of and launches attacks from a trusted device. In either case, the network sees all traffic as originating from a legitimate connected device.
Cisco CCNP SWITCH Recommended Switch Security
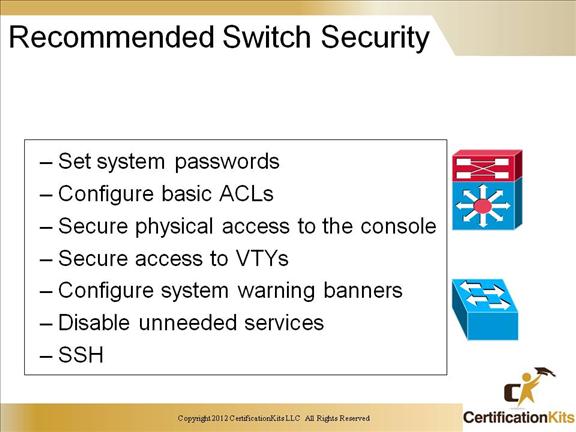
Other security recommendations are:
- • Trim CDP
- • Disable the integrated HTTP daemon
- • Configure basic logging
- • Secure SNMP
- • Limit trunking connections
- • Secure the spanning-tree topology
Cisco CCNP SWITCH Switched Port Analyzer
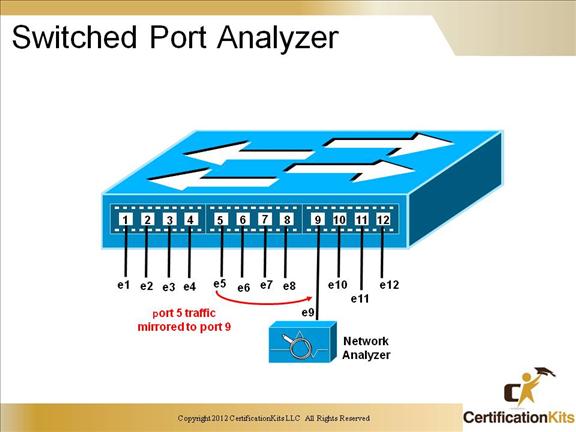
VLAN-base SPAN(VSPAN)
A variation of local SPAN where the source is a VLAN rather that a physical port
Local Span
Both the SPAN source and destination are located on the local switch. The source is one or more switch ports
Remote SPAN(RSPAN)
The SPAN source and destination are located on different switches. Mirrored traffic is copied over a special-purpose VLAN across trunks between switches from the source to the destination
Cisco CCNP SWITCH Authentication Methods

The AAA security services facilitate a variety of login authentication methods.
Basic Process for Configuring AAA
1. Enable AAA by using the aaa new-model global configuration command.
2. If a separate security server is used, configure security protocol parameters, such as RADIUS, TACACS+, or Kerberos.
3. Define the method lists for authentication by using an AAA authentication command.
4. Apply the method lists to a particular interface or line, if required.
Cisco CCNP SWITCH Configuring AAA Authentication
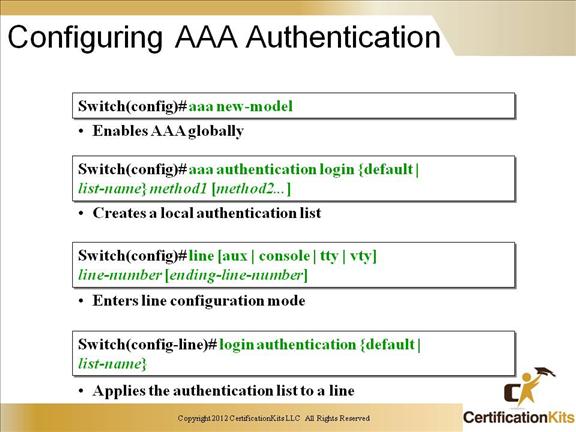
AAA functionality is an added layer of security that can be added to your switching environment. AAA will provide your network with Authentication, Authorization and Accounting features. The above example shows us the configuration tasks required for AAA Authentication. To configure Authorization, and Accounting features you would simply follow suit with the above configuration examples using the Authorization commands or the Accounting commands.
Cisco CCNP SWITCH 802.1x Port-Based Authentication
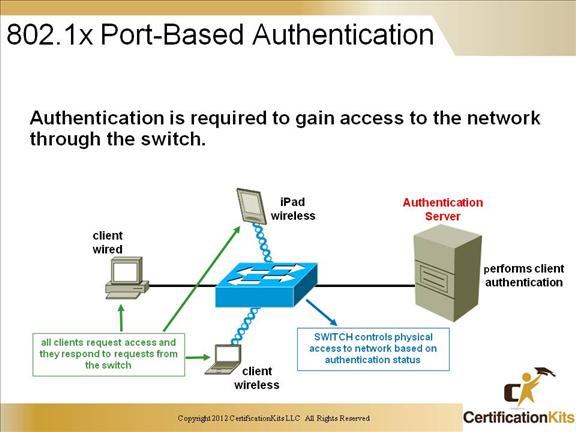
The IEEE 802.1x standard defines a port-based access control and authentication protocol that restricts unauthorized workstations from connecting to a LAN through publicly accessible switch ports. The authentication server authenticates each workstation that is connected to a switch port before making available any services offered by the switch or the LAN.
Until the workstation is authenticated, 802.1x access control allows only Extensible Authentication Protocol over LAN (EAPOL), Cisco switches also allow CDP and STP to pass before the authentication process.
Cisco CCNP SWITCH Configuring 802.1x
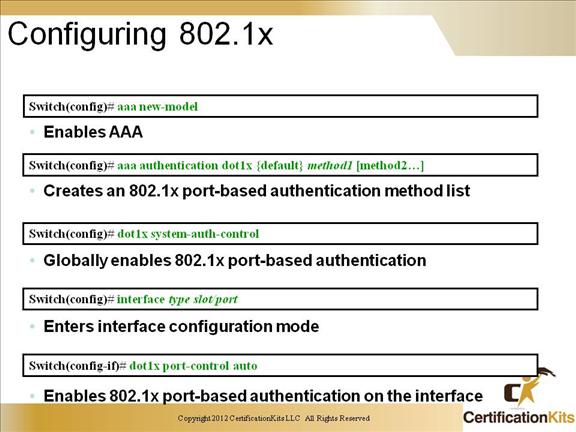
You control the port authorization state by using the dot1x port-control interface configuration command and these keywords:
force-authorized: Disables 802.1x port-based authentication and causes the port to transition to the authorized state without any authentication exchange required. The port transmits and receives normal traffic without 802.1x-based authentication of the client. This is the default setting.
force-unauthorized: Causes the port to remain in the unauthorized state, ignoring all attempts by the client to authenticate. The switch cannot provide authentication services to the client through the interface.
auto: Enables 802.1x port-based authentication and causes the port to begin in the unauthorized state, allowing only EAPOL frames to be sent and received through the port. The authentication process begins when the link state of the port transitions from down to up (authenticator initiation) or when an EAPOL-start frame is received (supplicant initiation). The switch requests the identity of the client and begins relaying authentication messages between the client and the authentication server. The switch uniquely identifies each client attempting to access the network by using the client MAC address.
Cisco CCNP SWITCH MAC Flooding Attack
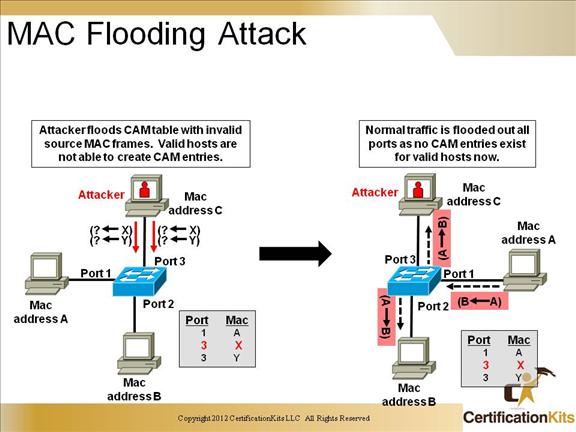
A common Layer 2 or switch attack as of this writing is MAC flooding, resulting in a switch’s CAM table overflow, which causes flooding of regular data frames out all switch ports. This attack can be launched for the malicious purpose of collecting a broad sample of traffic or as a denial of service (DoS) attack.
Cisco CCNP SWITCH Port Security
Port security is a feature supported on Cisco Catalyst switches that restricts a switch port to a specific set or number of MAC addresses.
– Can be learned dynamically or configured statically
– The port will then provide access to frames from only those addresses.
– Can limit based on a number of addresses
– Port security can be configured with “sticky learning,” available on some switch platforms, combines the features of dynamically learned and statically configured addresses. When this feature is configured on an interface, the interface converts dynamically learned addresses to “sticky secure” addresses. This adds them to the running configuration as if they were configured using the switchport port-security mac-address command.
Cisco CCNP SWITCH Configuring Port Security on a Switch
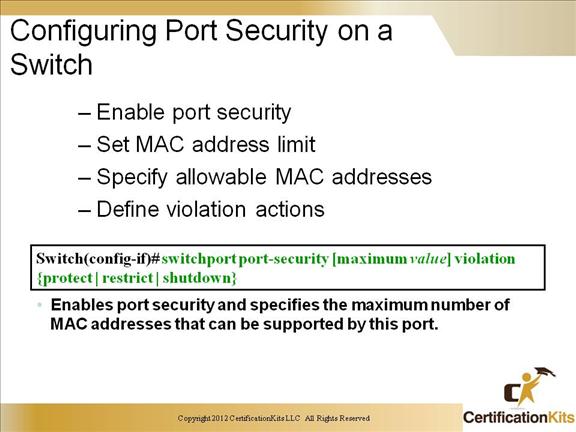
Enables port security.
Switch(config-if)#switchport port-security
Sets a maximum number of MAC addresses that will be allowed on this port. Default is one.
Switch(config-if)#switchport port-security maximum value
Specifies which MAC addresses will be allowed on this port (optional).
Switch(config-if)#switchport port-security mac-address mac-address
Defines what action an interface will take if a nonallowed MAC address attempts access.
Switch(config-if)#switchport port-security violation {shutdown | restrict | protect}
Cisco CCNP SWITCH Network Access Port Security
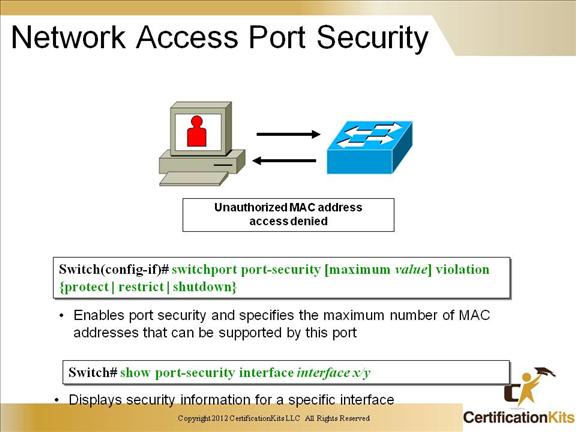
Port security is a MAC address lockdown that disables the port if the MAC address is not valid. You can use the show port security address command in order to view the learned or statically assigned MAC addresses.
Switch# show port-security address
Secure Mac Address Table
——————————————————————-
Vlan Mac Address Type Ports Remaining Age
(mins)
—- ———– —- —– ————-
1 0001.0001.0001 SecureDynamic Fa5/1 15 (I)
1 0001.0001.0002 SecureDynamic Fa5/1 15 (I)
1 0001.0001.1111 SecureConfigured Fa5/1 16 (I)
1 0001.0001.1112 SecureConfigured Fa5/1 –
1 0001.0001.1113 SecureConfigured Fa5/1 –
1 0005.0005.0001 SecureConfigured Fa5/5 23
1 0005.0005.0002 SecureConfigured Fa5/5 23
1 0005.0005.0003 SecureConfigured Fa5/5 23
1 0011.0011.0001 SecureConfigured Fa5/11 25 (I)
1 0011.0011.0002 SecureConfigured Fa5/11 25 (I)
——————————————————————-
Total Addresses in System: 10
Max Addresses limit in System: 128
Cisco CCNP SWITCH Types of ACLs
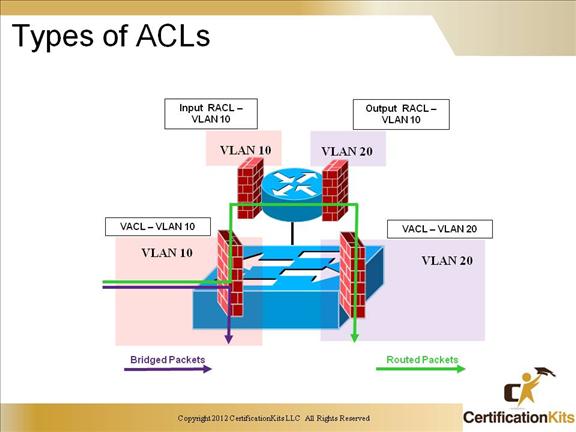
Access List, on a switch? Sure enough. As a matter of fact you can use 2 different types of Access List on a switch. What are they called? VLAN Access Control Lists and Router ACLs.
VACL: Also known as VLAN maps.
Virtual LAN (VLAN) access control lists (ACLs), or VACLs, control the redirection of all packets on a Catalyst 6000 family switch via a Policy Feature Card (PFC). VACLs, which are for security packet filtering, enable you to redirect traffic to specific physical switch ports. Unlike IOS ACLs, VACLs are not direction-specific. They automatically capture traffic traveling both inbound and outbound.
Router ACL:
The name kinda explains itself. This is the type of ACL we would configure on our normal routing and switching devices. Router ACLs can be applied to the input and output directions of a VLAN interface. Only router ACLs can be applied to a VLAN interface. VLAN maps and router ACLs can be used in combination, i.e., used on 3550 switches.
Cisco CCNP SWITCH Configuring VACLs
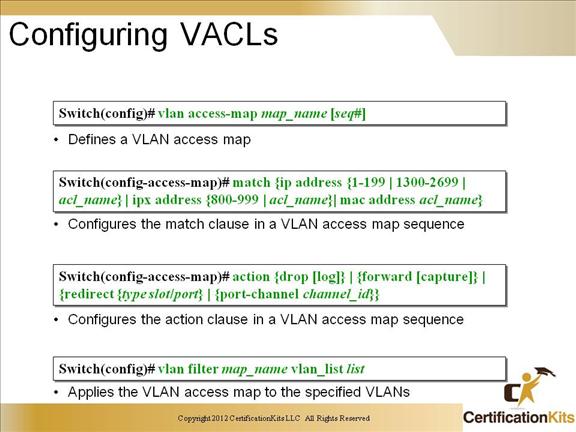
Unlike SPAN, VACLs give you a much higher degree of control over the type of traffic that you want to capture. You can capture traffic based on the source IP address or the destination IP address, as well as specifying a specific IP protocol number. Depending on the IP protocol chosen, you may also be able to specify other parameters as well. With TCP, for instance, you can specify both the source and destination ports, and limit the capture to only packets from established TCP connections. Furthermore, your Multilayer Switch Feature Card (MSFC) can utilize flows to effectively ensure that packets sent between different VLANs will cross the switch’s backplane only once, eliminating duplicate packets being captured.
