In preparation of our CCNA exam, we want to make sure we cover the various concepts that we could see on our Cisco CCNA exam. So to assist you, below we will discuss Cisco Switching Cliff Notes.
LAN Switching
Layer 2 Switching
Approximately 20% of your Cisco CCNA exam will be dedicated to Switching. You want to make sure you are well versed in the various terms which will undoubtedly appear on your CCNA exam so you are not caught off guard. Below we will cover the major switching topics you will encounter on your Cisco CCNA exam.
Bridges and Cisco switches are devices that segment or break-up collision domains on a network. They are important components of a network infrastructure and function at the access layer and are definately covered on the CCNA exam. Layer 2 switching is hardware based, it uses MAC addresses to filter the network which results in wire speed, low latency and low cost.
Cisco Switches vs Bridges
Layer 2 Switching
Carrier Sense Multiple Access Collision Detect works as follows:
Switch's three functions at Layer 2
1. Address learning: Associates every received source MAC address with a local port and builds the CAM table(or MAC Table).
2. Forward/filter decisions: If destination MAC address is in the CAM Table and is associated with a port, it will send it to that port; otherwise the frame will be forwarded to all ports except the receiving port.
3. Loop avoidance: Uses STP to avoid loops.
Spanning-Tree Protocol(STP)
STP is a concept that definately trips people up on their CCNA exam. So take your time in reviewing these concepts.
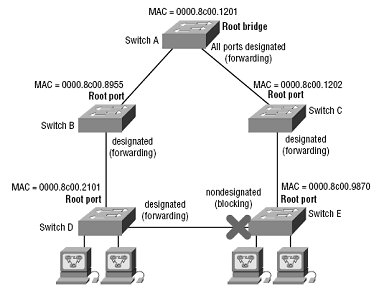
Root Bridge
Non – Root Bridge
Spanning – Tree Port State
Blocking: Won't forward frames; listens to BPDUs. All ports are in this state when the switch is powered up.
Listening: Also listens to BPDUs and makes sure it will not create loops.
Learning: Learns MAC addresses and Builds the CAM table.
Forwarding: Sends and receives data.
LAN Switching Types
Store and Forward: the complete frame is received on the switch’s buffer; a CRC is run, and then forwarded to its destination.
Fragment Free: Checks the first 64 bytes of a frame for fragmentation before forwarding. This would include the preamble, destination address, source address and length.
Cut-through: Once the destination MAC is received (first 13 bytes), the frame is forwarded to its destination. This would include only the preamble and destination address.
Managing Cisco 2950 Switch
switch# show mac-address-table
Port Security
switch(config-if)# switchport mode access Define a port as not connected to another switch.
switch(config-if)# switchport security Enable switch port security on this interface.
switch(config-if)# switchport port-security mac-address mac-address Allow access to this MAC address.
switch(config-if)# switchport port-security maximum value Maximum number of authorized MAC addresses (1-132).
switch(config-if)# switchport port-security violation [protect | restrict | shutdown]
switch(config-if)# switchport port-security mac-address sticky sw# show port-security interface interface-id Show interface security status.
switch# show port-security address Show secured MAC addresses and their associated interface.
EtherChannel
Rapid STP (RSTP) – IEEE 802.1w
Edge Type Connection: Connection between an end user and a switch or a hub
1- Alternate port: If the root port stop receiving BPDU from the root bridge, the alternate port becomes the root port.
2- Backup port: A port in disregarding state connected to the same segment where another port on the same switch is in forwarding state. If the forwarding port link fails, the backup port becomes forwarding port.
3- Disabled port: administratively disabled.
I hope you found this article to be of use and it helps you prepare for your Cisco CCNA certification. Achieving your CCNA certification is much more than just memorizing Cisco exam material. It is having the real world knowledge to configure your Cisco equipment and be able to methodically troubleshoot Cisco issues. So I encourage you to continue in your studies for your CCNA exam certification.
