It looks like some recent NSA document leaks may suggest that the Cisco PIX and ASA firewalls have the ability to be compromised by the NSA. It appears that a firmware implant for both the ASA and PIX devices called JETPLOW can be deployed on a firewall target with an exfiltration path to the NSA’s Remote Operations Center. It seems that as long as DNT’s BANANAGLEE software implant is on the Cisco PIX or ASA firewall, JETPLOW can be remotely installed and upgraded. It’s backdoor is pretty far reaching from what we are hearing.
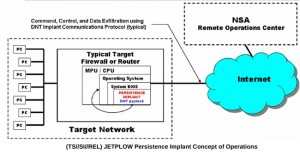
Cisco ASA Exploit
It seems that this has not only impacted Cisco firewall devices, it is being reported that this extends to Juniper, Huawei and other products such as HP server, Dell servers, and more. Obviously we can’t confirm all of this. But it is something to think about. Here is some of the other information being distributed.
Some comments from industry leaders such as Cisco is they are very concerned about the integrity of their products when something like this happens. Based on the fact that Huawei were impacted, you might assume that there was no cooperation from the companies impacted as it is hard to imagine foreign companies agreeing to such a backdoor exploit.
This is Cisco’s response:
The company also published an official security response late on Sunday, saying it had requested Der Spiegel‘s documents and noting that “Cisco development policies prohibit any product behaviors that weaken the security posture of a Cisco device.” This document may not be useful just yet, but it could be updated in future as and when the company has more to tell its customers.
A Juniper spokesperson echoed the same sentiments. “We take allegations of this nature very seriously and are working actively to address any possible exploit paths … We are also committed to the responsible disclosure of security vulnerabilities, and if necessary, will work closely with customers to implement any mitigation steps,” the spokesperson said. “Juniper Networks is not aware of any so-called ‘BIOS implants’ in our products and has not assisted any organization or individual in the creation of such implants.”
Finally, think this doesn’t impact most people. Not only were networking devices compromised, but we see that on the list below there are exploits for motherboard BIOS systems that use System Management Mode.
So how far reaching was the exploit? The reports are there were 258 successfully infiltrated targets across 89 countries.
Ok, some more info we are seeing.. the USB cable exploit seems to have a circuit board installed in the USB cable can install the exploit onto target PCs AND onto target networks via a wireless bridge. Wooow! Not to stop there, we also are hearing aout Wi-Fi exploits under code name NIGHTSTAND and code name PICASSO collects user data from GSM wireless phones!
So why was this done and which group in the NSA was responsible for this? Reports suggest that the ANT specialists (Advanced Network Technology) associates of the TAO( Tailored Access Operations) group who are skilled in hacking and data skimming techniques. This division does not just manufacture the hardware, it also creates the software code behind the exploits.
Update
The NSA seems to have a smorgasbord of options to take over remote devices. One of the ways is to even have he NSA to intercept a shipment of networking gear going from the vendor to customer and then the NSA will install it’s backdoor exploit on the device. Another that has been mentioned is the NSA can even review the Windows crash dumps that are sent to Microsoft from your PC and use data from that to exploit a PC. Other reports state that there are various exploits that are commonly used to remote controll iOS devices(iPhones and iPads) and any GSM based cell phone. Finally, there is the NIGHTSTAND exploit which is for your WI-FI 802.11 setups that in a perfect scenario can be deployed from 8 miles away! How many ex-husbands and ex-wives wish they had this at their disposal!
Now another piece of interesting news is that Cisco is stating that all US networking devices are required by law to have surveillance capabilities built-into them. This is for legitimate court ordered wiretaps and the such. But the key here is it seems that Cisco is indicating that the NSA was not leveraging these features, but the reported exploits that are noted above.
Firewalls:
(1) Cisco PIX and ASA: Codename “JETPLOW”
(2) Huawei Eudemon: Codename “HALLUXWATER”
(3) Juniper Netscreen and ISG: Codename: “FEEDTROUGH”
(4) Juniper SSG and Netscreen G5, 25, and 50, SSG-series: Codename:
“GOURMETTROUGH”
(5) Juniper SSG300 and SSG500: Codename “SOUFFLETROUGH”
Routers:
(1) Huawei Router: Codename “HEADWATER”
(2) Juniper J-Series: Codename “SCHOOLMONTANA”
(3) Juniper M-Series: Codename “SIERRAMONTANA”
(4) Juniper T-Series: Codename “STUCCOMONTANA”
Servers:
(1) HP DL380 G5: Codename “IRONCHEF”
(2) Dell PowerEdge: Codename “DEITYBOUNCE”
(3) Generic PC BIOS: Codename “SWAP”, able to compromise Windows, Linux,
FreeBSD, or Solaris using FAT32, NTFS, EXT2, EXT3, or UFS filesystems.
USB Cables and VGA Cables:
Codename “COTTONMOUTH”, this one is a hardware implmant hidden in a USB
cable. The diagram shows it’s small enough that you would never know its
there.
Codename “RAGEMASTER”, VGA cable, mirrors VGA over the air.
